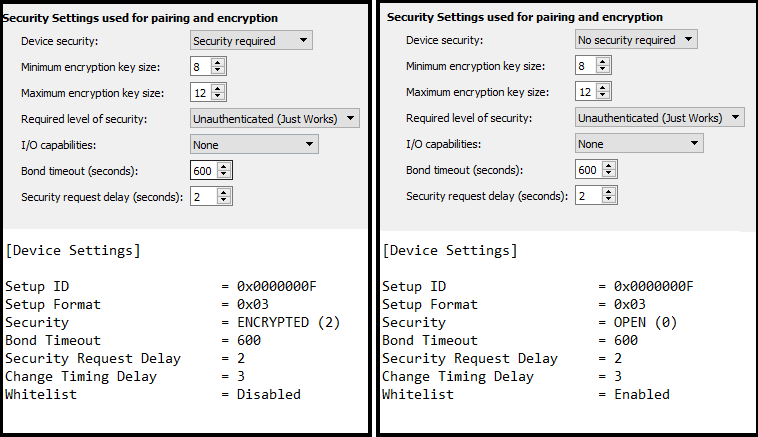
I’m trying to create a nRF8001 device without the need for any keys, because the device will be inaccessible in mounted condition. Additionally the connection must be secured and unauthenticated (just Works).
In case a new peer device is requesting bonding procedure with my already paired nRF8001-Device, the pairing information is going to be deleted. On the second connection attempt pairing information is deleted and a secured connection can be established.
This works fine with modern Android devices with random resolvable private addresses. However this does not work with my old HTC One (Android 5.0.2) with a public address chip. In case the nRF8001-Device has been bonded with a public address peer, SCAN_REQ and CONNECT_REQ packages are ignored.
Here is a commented sniffer record: public_address_anomaly.pcapng
I read about nRF8001 whitelist setting on link text but the setting is disabled.
Did I miss anything? Is there a second parameter in setup data that must be altered? Is there a documentation of the volatile dynamic data structure? Can the dynamic data be changed to prevent this behaviour?