Environment :
-
Custom Board with MCU NordicSemi nRF51822-QFAA
-
Softdevice S110 7.1
-
IAR for ARM 7.1
-
SDK 7.2 using a merged service (HID keyboard example + NUS example + HRS example)
-
Testing with iPhone 5S, 6 and iPad air (iOS 8.1.3)
/ Nexus 5 and Galaxy Note 3 (Android 4.4.2).
/*********************************************************************************/
Hello, I'm using BLE Sniffer 0.96 provided by Nordic.
This is a magnificent tool.
I wonder this could analyze the packets which are send to the bonded smart phones.
Similary, the Android App Master Control App provides similar function like the picture below.
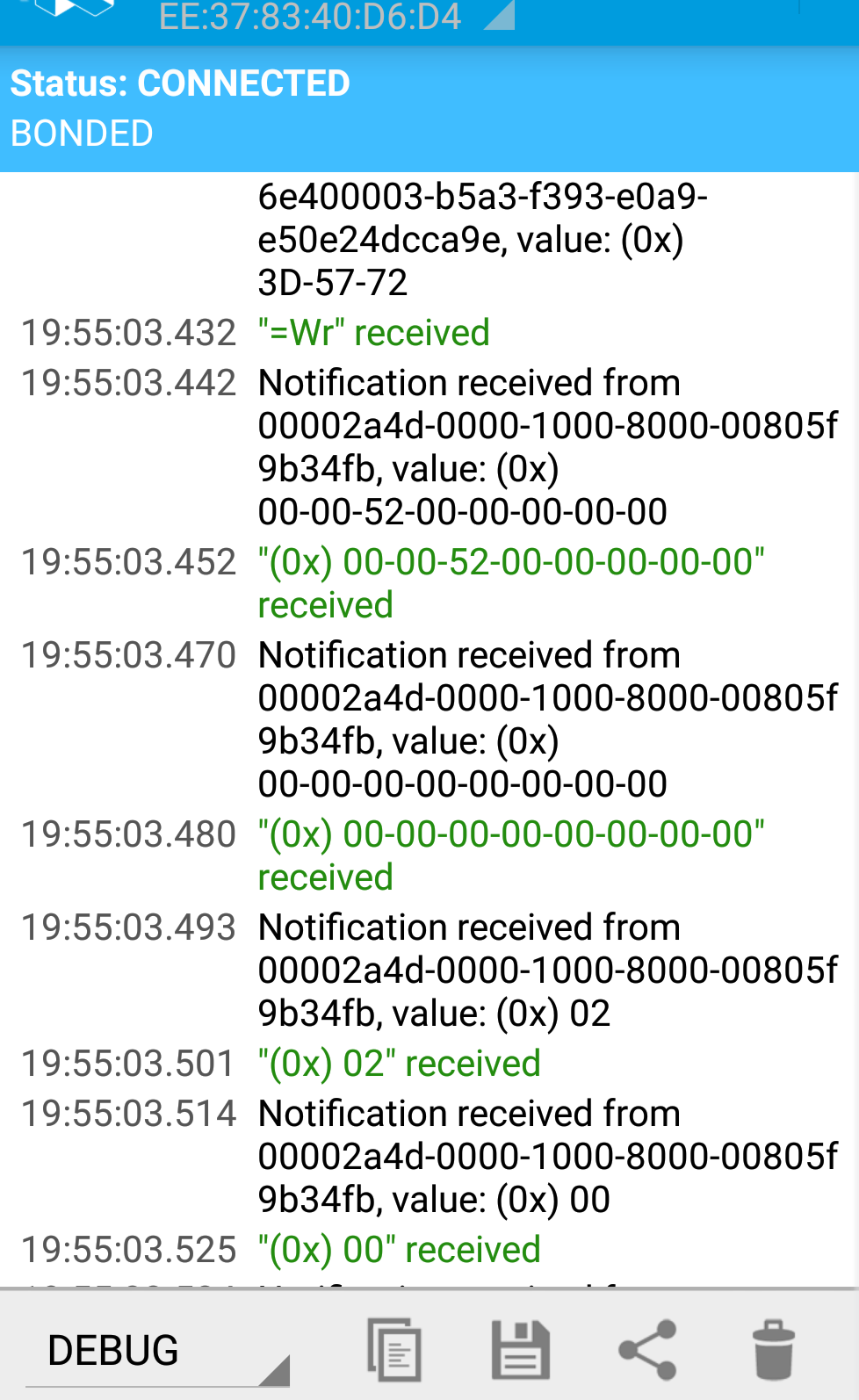
(The App shows the key values and the UART strings.)
So, does the BLE Sniffer could do something like this?
Or does the Wireshark can filter out the packets I send?
Since I cannot always turn on the Master Control App when I demonstrate,
I hope there is a feature like this.
-Regards, Mango922
/*********************************************************************************/
Added : Nordic_Keyboard example 7.2 sniff.pcapng
Here it is. I used BLE Sniffer 1.0.1 as you told. My laptop is Samsung R440 (Windows 7 SP1 32bit).
My Wireshark version is Wireshark-win32-1.10.11.
This file is the pcapng file when I downloaded the HID Keyboard Example (SDK 7.2) to my
custom board. I connected to my iPhone 5S (iOS 8.1.3).
This sniffed only the pairing process.
I did not sniffed when I pressed the button which sends "hello".
The CONNECT_REQ packet is the 149th packet.
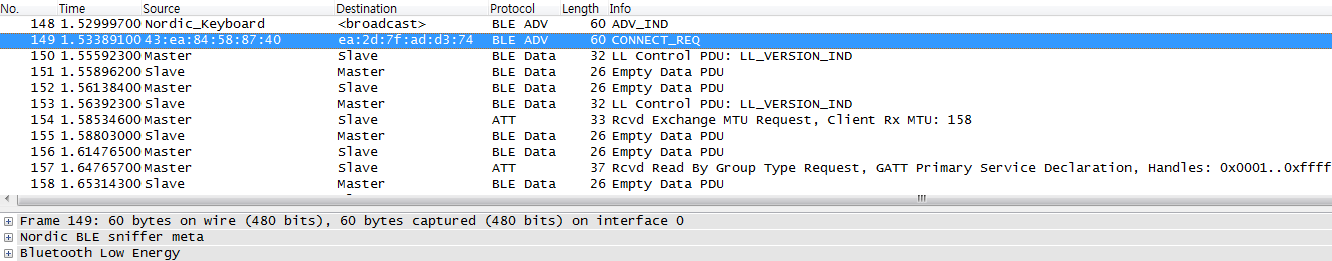
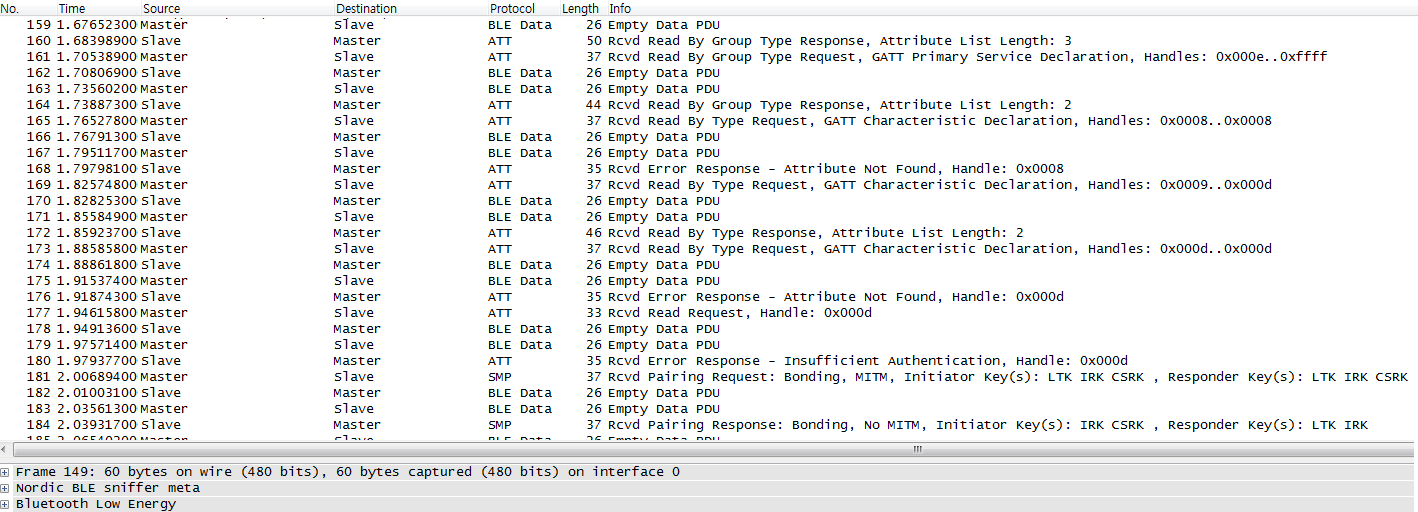
What should be the next step in order to sniff the HID packets?
