I successfully enabled littlefs in mcuboot and read/write it successfully (due to project requirements), and then tried to enable littlefs in both mcuboot and app, operating on the same lfs partition. However, I received an error message during the build process, indicating that the partition does not meet the requirements? Or something else. I have tried to make a static partition table with LFS enabled separately in mcuboot or in the app, but there has been no improvement. How can I solve the problem of this partition not meeting the requirements?
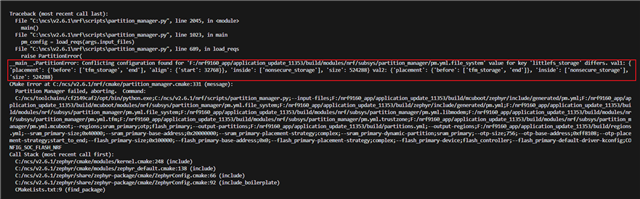
In addition, I have made many different attempts based on the error content, and personally think it may be related to TFM? Could it be because mcuboot and the app run in different trust zones that their littlefs zones conflict?


