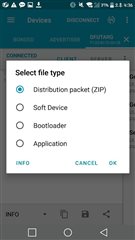
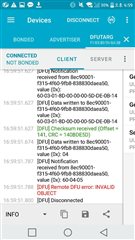
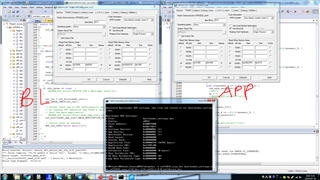
The nRF52832 chip and SDK12.3.0 implement the buttonless DFU function.
First, as you are guided by the DK board, you have already completed the tutorial.
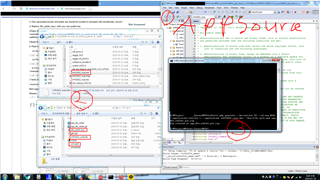
I tried to run it in the source of my project,
My project device is stopped during the initial setup of the application and it seems to run in bootloader mode.
In my project, I did not call the bootloader mode setting function, but only added the header file and C file.
I want to know the exact reason for this and how to solve it.
Why do I enter this mode when I did not call the bootloader mode function?
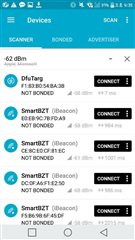
bootloader mode is running but not advertising.
I'm guessing now that my device's state is bootloader mode, but I'm not sure.
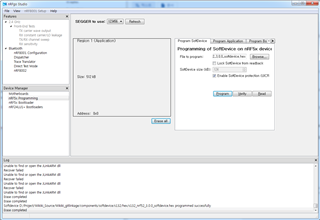
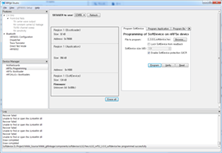
Softdevice & firmware all delete picture
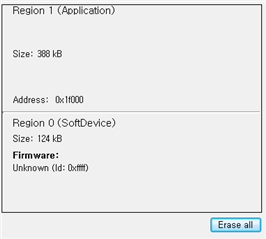
Softdevice & My DFU Project Downloaded on Chip
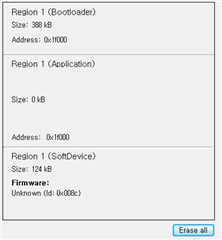
Help me...Thank you very much.





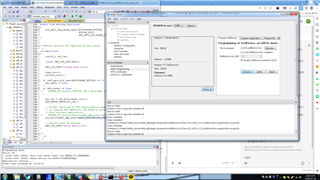
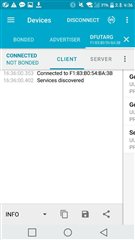
 This log is the log that attempted the DFU function a few minutes ago.
This log is the log that attempted the DFU function a few minutes ago.