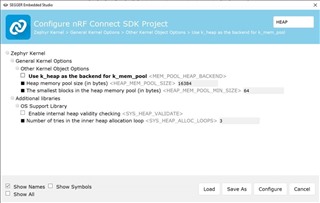
Hi,
I can run the following code within main.c successfully, but it produces the error as shown in the attachment upon execution of k_free(mem.ptr) from with aggregator.c. Any ideas why it is not working?
char *mem_ptr;
mem_ptr = k_malloc(200);
if (mem_ptr != NULL) {
memset(mem_ptr, 0, 200);
printk("Memory allocated:");
}
else
{
printk("Memory not allocated:\n");
}
k_free(mem_ptr);
printk("Memory released:\n");