I am developing an applicaiton to run on the app core of an nRF5340, and I have mcuboot enabled for the purposes of handling DFU.
I have recently implemented signing the app firmware with our own pem key instead of using the default key provided by mcuboot.
I am raising this support request as there does not seem to be a set ideal way to accomplish this automatically. If have tried two methods, and since upgrading to v1.5.0 have changed to using Method B.
Method A)
Specify in cmakelists.txt that we are in charge of the config of mcuboot e.g. via
set(mcuboot_CONF_FILE
${CMAKE_CURRENT_SOURCE_DIR}/boards/mcuboot.conf
)
| Advantages | Disadvantages |
| Uses the immediate path of the conf file, so we can have the pem file inside our repository rather than the nRF Connect SDK source tree | Have to maintain the full conf info for mcuboot, which generally changes in configuration between SDK revisions. Several changes observed going from v1.4.2 to v1.5.0 |
| Goes against the idea of having the child_image directory to control small tweaks to the standard configuration of mcuboot that has been added in v1.5.0 |
Method B)
Use child_image mcuboot conf file to specifiy the pem file
| Advantages | Disadvantages |
| Don't have to maintain a full conf file for mcuboot | Have to copy it into mcuboot area of SDK source code checkout. This is the only Path it looks in, and full paths are 1. a bit unworkable and 2. discouraged. |
| Having it stored at this path seems to trigger the cmake warning regarding using standard mcuboot key and that it should not be used in production, which is confusing to say the least. See warning below |
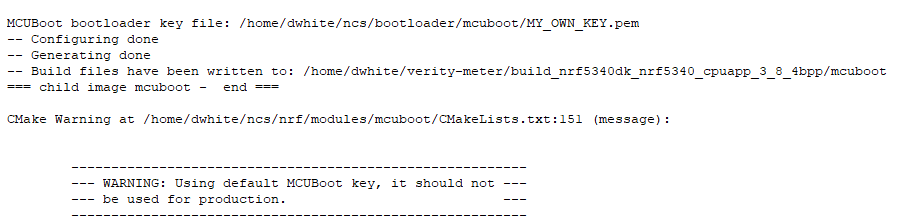
Am I missing something here, or are these the simplest options.


