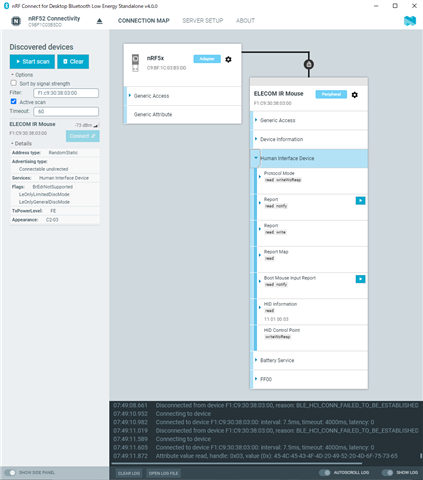
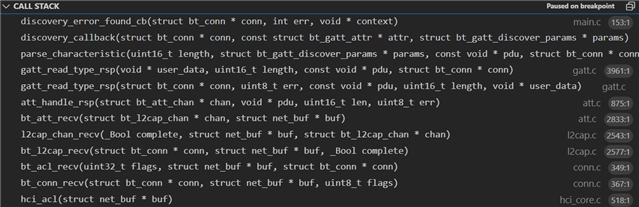
Hi, I tested Central HIDS example in nRF Connect SDK 2.1.0 with NRF52840DK. The example works with my BLE keyboard, but does not work with my BLE mice. The followings are messages for the BLE mice. How can I modify the example to connect them? The first mouse can connect with nRF Connect for Desktop, and the other can't. I have attached the connection information.
# ELECOM M-BY10BR
Filters matched on UUID 0x1812.
Address: F1:C9:30:38:03:00 (random) connectable: yes
Connected: F1:C9:30:38:03:00 (random)
Security changed: F1:C9:30:38:03:00 (random) level 2
The discovery procedure failed with -3
Disconnected: F1:C9:30:38:03:00 (random) (reason 8)
# SANWA SUPPLY MA-BTBL155R
Filters matched on UUID 0x1812.
Address: CB:D4:5B:20:AA:57 (random) connectable: yes
Connected: CB:D4:5B:20:AA:57 (random)
Failed to set security: -12
The service could not be found during the discovery
Disconnected: CB:D4:5B:20:AA:57 (random) (reason 62)