Hi,
I just spend a day trying to get the nrf_sniffer tool working.
The devzone.nordicsemi.com/.../ contained some very useful info but unfortunately it seems i am now stranded at a dead end.
First something that is not yet mentioned in that post: the serial lib does not work with higher numbered com ports. Eg I have already plugged a lot of ftdi cables in my pc and it got com port number 135. That does not work, only after i moved it to com port 5 the python code starting seeing the com port.
So after this point for about 1 happy second it seemed to be working showing packets in wireshark but then it just stopped. Quiting wireshark and starting it again and I got greeted with the following error: 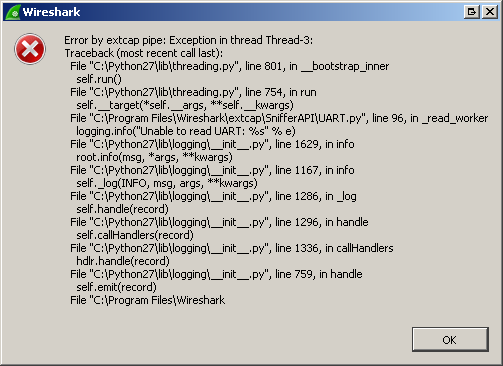
Stopping wireshark again and unplugging replugging the board and it works again for a second. Stopping wireshark and connecting to the comport with teraterm and it shows a lot of data being output (unreadable hex i suppose or i am at the wrong baud rate).
So wild guess would be that the python part does not work correctly in processing the incoming data.... any suggestions ?
I also tried on a second windows 7 PC. There I do not even get the one second of good packets though i only tried twice (no packets at all). If i check with teraterm it still gives me a stream of data though so that part seems again OK.
Version info: Windows 7 64bit
Wireshark 2.4.4
python-2.7.14
pyserial: 3.4
nrf_sniffer_2.0.0-beta-1_51296aa


