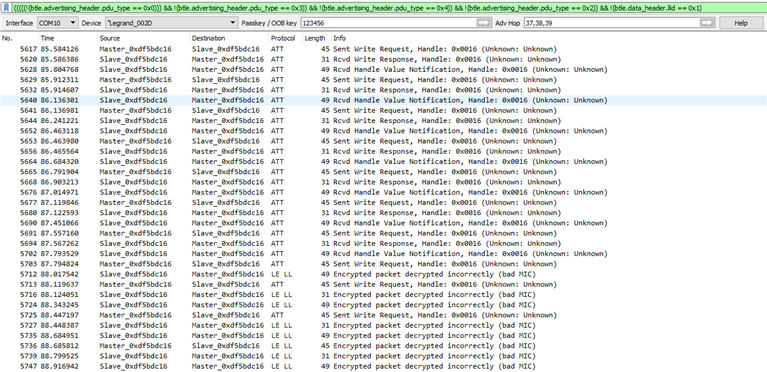
I want to sniff the connection between a Bluetooth Low Energy mouse (Logitech MX Master) and my smartphone (Samsung Galaxy Alpha). To do this I have tried to use the nRF-Sniffer in combination with an nRF51-DK as well as an nRF52-preview-DK board (compatible hex file was provided by Aryan here). My operating system is Windows 7 Enterprise (64 bit), Wireshark version is 1.12.6.
Sniffing the initial connection is working as expected, but after a couple of seconds all packets are marked with an error: "Encrypted packet decrypted incorrectly (bad MIC)". I'm not a Bluetooth expert (yet), but I think that the sniffer should be able to decrypt all packets as he is listening to the connection from the very beginning. Traces are attached to this post. What am I doing wrong? Isn't it possible to sniff the communication for a longer time?
Trace with nRF51-DK: Logitech_MX_Samsung_Alpha_nrf51.pcapng
Trace with nRF52-preview-DK: Logitech_MX_Samsung_Alpha_nrf52.pcapng
Update (August 17): In the meantime I have reproduced this observation on a Linux system using the Python API. The effect is probably related to the board itself (or the software it is running), not the host computer.