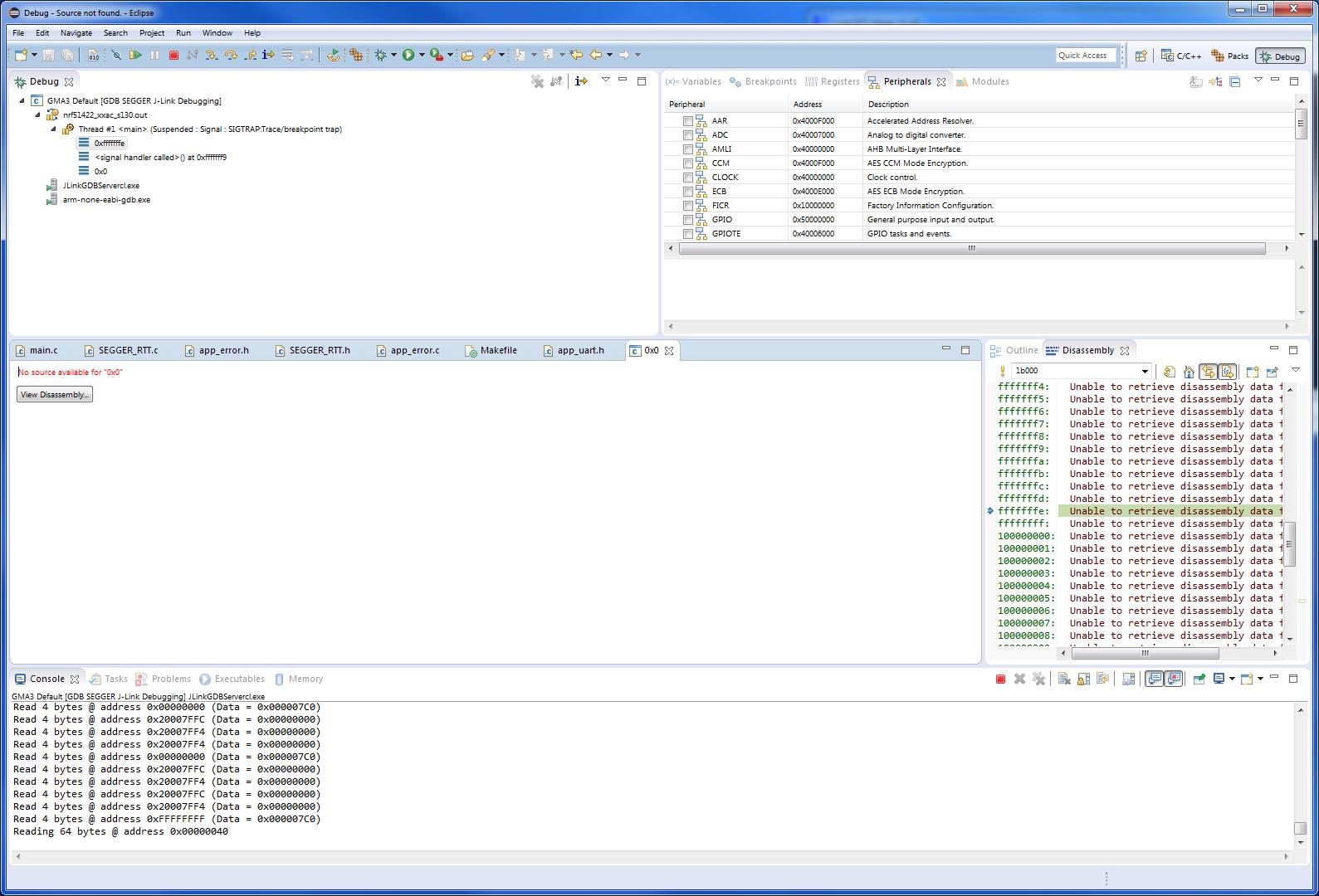
I followed the instructions and comments in devzone.nordicsemi.com/.../ . I built a project around the ble_app_gls example (with a couple of minor changes such as using -DNRF_LOG_USES_RTT=1) . The project compiles and runs just fine if I run it under Keil. It also compiles with no errors or warnings and appears to flash correctly under Eclipse/GCC. However, with GCC, I see: (1) no output on the RTT viewer, (2) in the Debug frame, "no source available for 0x0"
Here's the console transcript: SEGGER J-Link GDB Server V5.10i Command Line Version
JLinkARM.dll V5.10i (DLL compiled Jan 28 2016 09:38:53)
-----GDB Server start settings----- GDBInit file: none GDB Server Listening port: 2331 SWO raw output listening port: 2332 Terminal I/O port: 2333 Accept remote connection: localhost only Generate logfile: off Verify download: on Init regs on start: on Silent mode: off Single run mode: on Target connection timeout: 0 ms ------J-Link related settings------ J-Link Host interface: USB J-Link script: none J-Link settings file: none ------Target related settings------ Target device: nRF51822_xxAA Target interface: SWD Target interface speed: 4000kHz Target endian: little
Connecting to J-Link... J-Link is connected. Firmware: J-Link Lite-Cortex-M V8 compiled Aug 20 2015 17:57:19 Hardware: V8.00 S/N: 518110857 Feature(s): GDB Checking target voltage... Target voltage: 3.30 V Listening on TCP/IP port 2331 Connecting to target...Connected to target Waiting for GDB connection...Connected to 127.0.0.1 Reading all registers Read 4 bytes @ address 0x00000000 (Data = 0x000007C0) Read 2 bytes @ address 0x00000000 (Data = 0x07C0) Target interface speed set to 1000 kHz Resetting target Halting target CPU... ...Target halted (PC = 0x000006D0) R0 = FFFFFFFF, R1 = FFFFFFFF, R2 = FFFFFFFF, R3 = FFFFFFFF R4 = FFFFFFFF, R5 = FFFFFFFF, R6 = FFFFFFFF, R7 = FFFFFFFF R8 = FFFFFFFF, R9 = FFFFFFFF, R10= FFFFFFFF, R11= FFFFFFFF R12= FFFFFFFF, R13= 000007C0, MSP= 000007C0, PSP= FFFFFFFC R14(LR) = FFFFFFFF, R15(PC) = 000006D0 XPSR C1000000, APSR C0000000, EPSR 01000000, IPSR 00000000 CFBP 00000000, CONTROL 00, FAULTMASK 00, BASEPRI 00, PRIMASK 00 Reading all registers Read 4 bytes @ address 0x000006D0 (Data = 0x4C174916) Read 2 bytes @ address 0x000006D0 (Data = 0x4916) Select auto target interface speed (2000 kHz) Flash breakpoints enabled Semi-hosting enabled (Handle on BKPT) Semihosting I/O set to TELNET Client SWO disabled succesfully. SWO enabled succesfully. Read 4 bytes @ address 0x000006D0 (Data = 0x4C174916) Read 2 bytes @ address 0x000006D0 (Data = 0x4916) Downloading 4096 bytes @ address 0x0001B000 - Verified OK Downloading 4096 bytes @ address 0x0001C000 - Verified OK Downloading 4096 bytes @ address 0x0001D000 - Verified OK Downloading 4096 bytes @ address 0x0001E000 - Verified OK Downloading 4096 bytes @ address 0x0001F000 - Verified OK Downloading 4096 bytes @ address 0x00020000 - Verified OK Downloading 4096 bytes @ address 0x00021000 - Verified OK Downloading 4096 bytes @ address 0x00022000 - Verified OK Downloading 4096 bytes @ address 0x00023000 - Verified OK Downloading 4096 bytes @ address 0x00024000 - Verified OK Downloading 4096 bytes @ address 0x00025000 - Verified OK Downloading 4096 bytes @ address 0x00026000 - Verified OK Downloading 4096 bytes @ address 0x00027000 - Verified OK Downloading 4096 bytes @ address 0x00028000 - Verified OK Downloading 3748 bytes @ address 0x00029000 - Verified OK Downloading 8 bytes @ address 0x00029EA4 - Verified OK Downloading 148 bytes @ address 0x00029EAC - Verified OK Comparing flash [....................] Done. Verifying flash [....................] Done. Writing register (PC = 0x00028abc) Read 4 bytes @ address 0x00028ABC (Data = 0x480A2103) Read 2 bytes @ address 0x000226B2 (Data = 0x4B4A) Read 4 bytes @ address 0x000227DC (Data = 0x00029950) Read 2 bytes @ address 0x000226B2 (Data = 0x4B4A) Resetting target Halting target CPU... ...Target halted (PC = 0x000006D0) Read 2 bytes @ address 0x000226B2 (Data = 0x4B4A) Read 4 bytes @ address 0x000227DC (Data = 0x00029950) Read 2 bytes @ address 0x000226B2 (Data = 0x4B4A) Read 4 bytes @ address 0x000227DC (Data = 0x00029950) Read 2 bytes @ address 0x000226B2 (Data = 0x4B4A) R0 = FFFFFFFF, R1 = FFFFFFFF, R2 = FFFFFFFF, R3 = FFFFFFFF R4 = FFFFFFFF, R5 = FFFFFFFF, R6 = FFFFFFFF, R7 = FFFFFFFF R8 = FFFFFFFF, R9 = FFFFFFFF, R10= FFFFFFFF, R11= FFFFFFFF R12= FFFFFFFF, R13= 000007C0, MSP= 000007C0, PSP= FFFFFFFC R14(LR) = FFFFFFFF, R15(PC) = 000006D0 XPSR C1000000, APSR C0000000, EPSR 01000000, IPSR 00000000 CFBP 00000000, CONTROL 00, FAULTMASK 00, BASEPRI 00, PRIMASK 00 Reading all registers Read 4 bytes @ address 0x000006D0 (Data = 0x4C174916) Read 2 bytes @ address 0x000006D0 (Data = 0x4916) Setting breakpoint @ address 0x000226B2, Size = 2, BPHandle = 0x0001 Starting target CPU... ...Target halted (PC = 0xFFFFFFFE) Reading all registers Read 4 bytes @ address 0xFFFFFFFE (Data = 0x00000040) Read 2 bytes @ address 0xFFFFFFFE (Data = 0x0000) Removing breakpoint @ address 0x000226B2, Size = 2 Reading 64 bytes @ address 0x00000000 Read 4 bytes @ address 0x20007FFC (Data = 0x00000000) Read 4 bytes @ address 0x20007FF8 (Data = 0x00000000) Read 4 bytes @ address 0x00000000 (Data = 0x000007C0) Read 4 bytes @ address 0x20007FFC (Data = 0x00000000) Read 4 bytes @ address 0x20007FF4 (Data = 0x00000000) Read 4 bytes @ address 0x20007FF4 (Data = 0x00000000) Read 4 bytes @ address 0x00000000 (Data = 0x000007C0) Read 4 bytes @ address 0x20007FFC (Data = 0x00000000) Read 4 bytes @ address 0x20007FF4 (Data = 0x00000000) Read 4 bytes @ address 0x20007FFC (Data = 0x00000000) Read 4 bytes @ address 0x20007FF4 (Data = 0x00000000) Read 4 bytes @ address 0xFFFFFFFF (Data = 0x000007C0) Reading 64 bytes @ address 0x00000040
I tried manually using nrfjprog to load the hex files generated by gcc and by Keil. The Keil one executes, while the gcc one appears to do nothing at all, corresponding to the debugger indicating that the application is starting either at 0xFFFFFFFE or at 0x0.


