I am trying to perform the DFU on the nRF52 DK board from my esp32 board via Bluetooth with the following stack: Simple Management Protocol (SMP) + Bluetooth Low Energy (BLE).
I am using the commands format shown here: developer.nordicsemi.com/.../smp_protocol.html
and commands from image management group shown here: developer.nordicsemi.com/.../smp_group_1.html
I first try to get the state of images and I get the following notification back
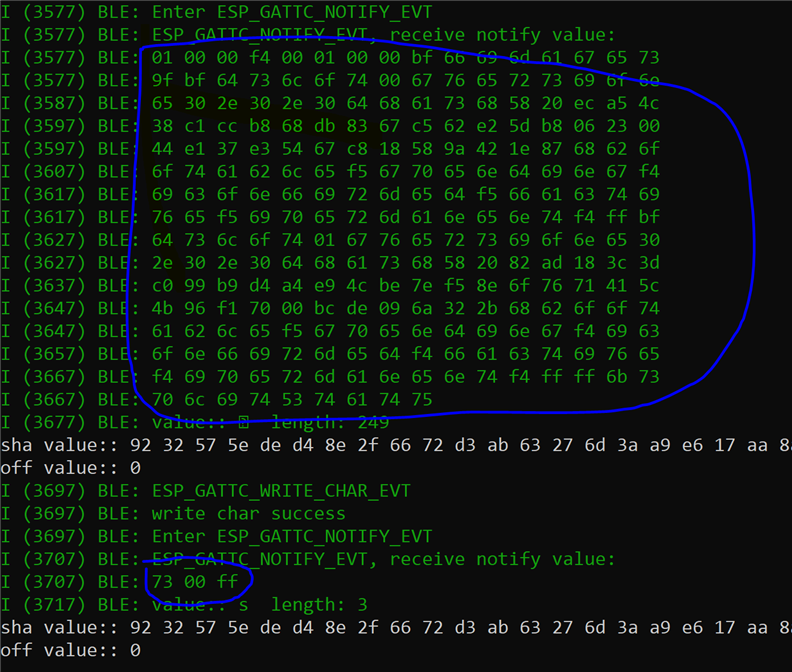
On checking for the data in CBOR i get proper values
1, 0, 0, false, 0, 1, 0, 0, {"images": [{"slot": 0, "version": "0.0.0", "hash": h'3B8B8664F91875B456BCC769242680B0657BD48A599A41B7F94CD83D89F4F32D', "bootable": true, "pending": false, "confirmed": true, "active": true, "permanent": false}, {"slot": 1, "version": "0.0.0", "hash": h'82AD183C3DC099B9D4A4E94CBE7EF58E6F7671415C4B96F17000BCDE096A322B', "bootable": true, "pending": false, "confirmed": false, "active": false, "permanent": false}], "splitStatus": 0}
where the initial 8 bits are response(though not mentioned on the above-mentioned webpage with command details) and then further expected response about the expected 2 images on the board.
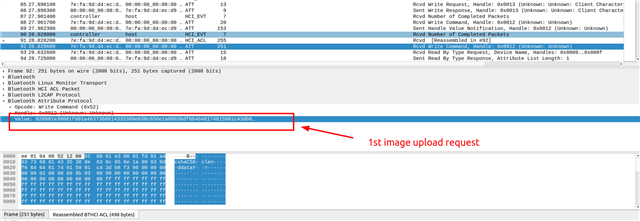
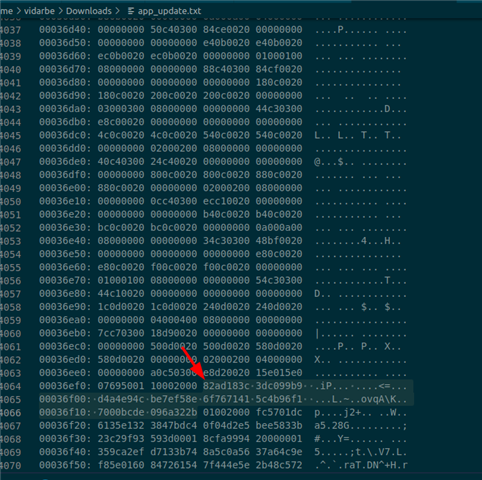
Next, I try to upload the image on the board in .bin format using the command shown on the webpage
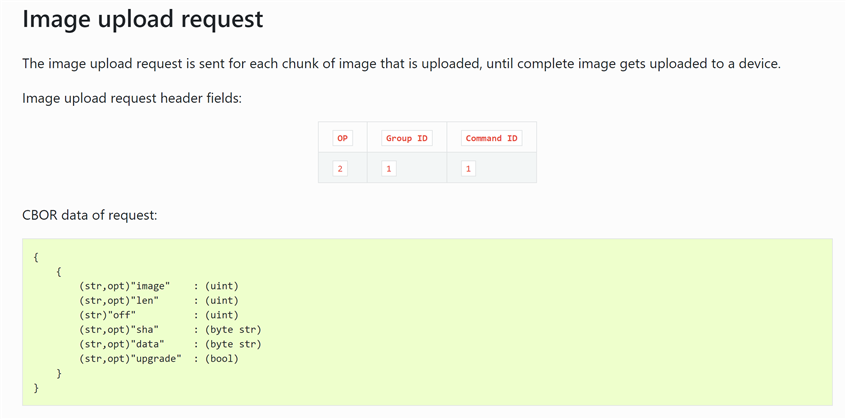
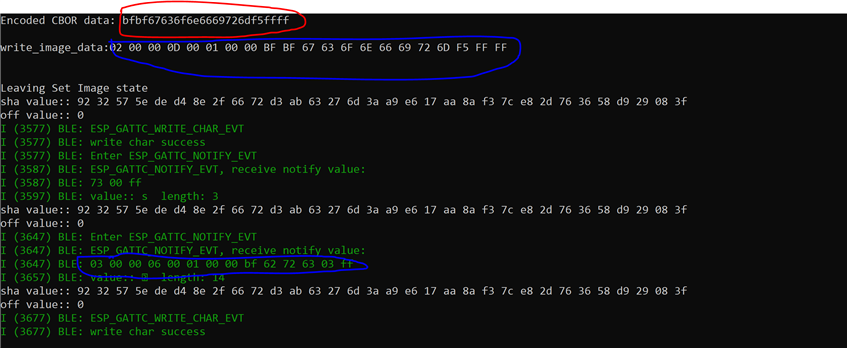
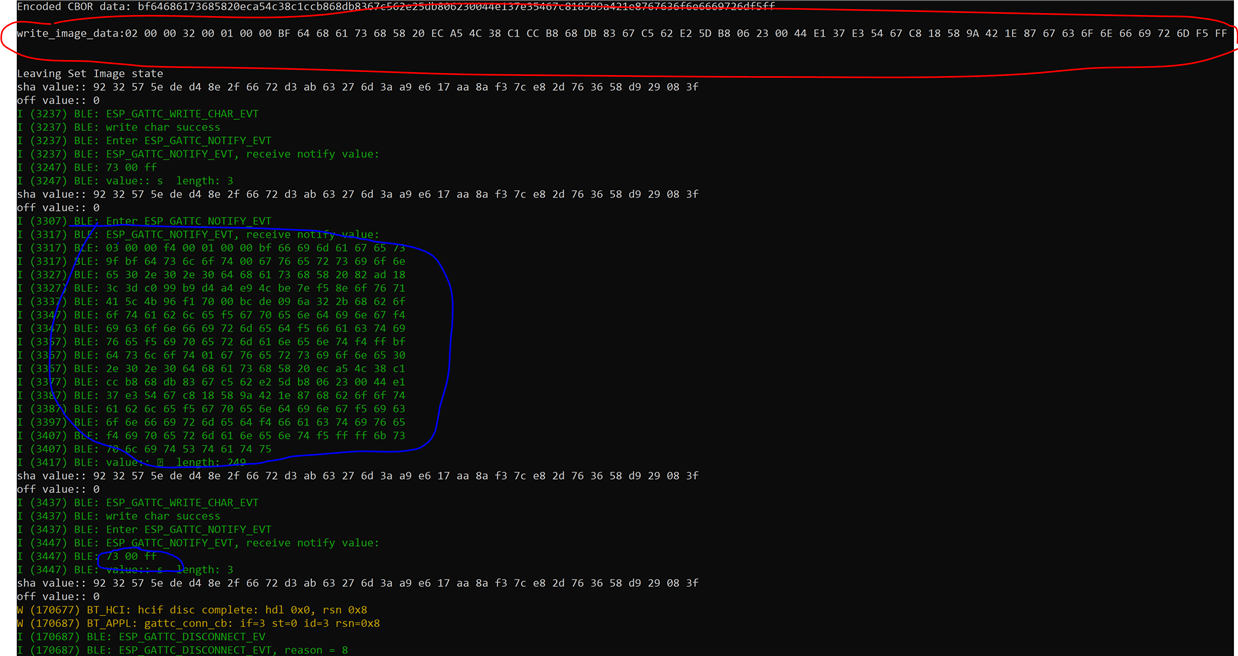
I am sending the following CBOR data(just few bytes for example, shown in red). The actual command +data and response is shown in blue. As evident from the response I get an error with error code 0x3. There is no RSN sent to get details. Now, I thought probably the data is not in the proper format or there is some discrepancy in the way CBOR data has been depicted to be sent on the webpage. So, I tried sending in a format where there is CBOR data within single brackets { ..} instead of two brackets(which(two brackets) I find absurd as any CBOR decoder is not able to handle it). If I send it within single brackets I again get back error. I tried only the compulsory field of offset and data in the first packet and also the proper format for first packet with all fields for offset 0. Still I keep getting response with error code 0x3. I tried multiple combinations but nothing works.
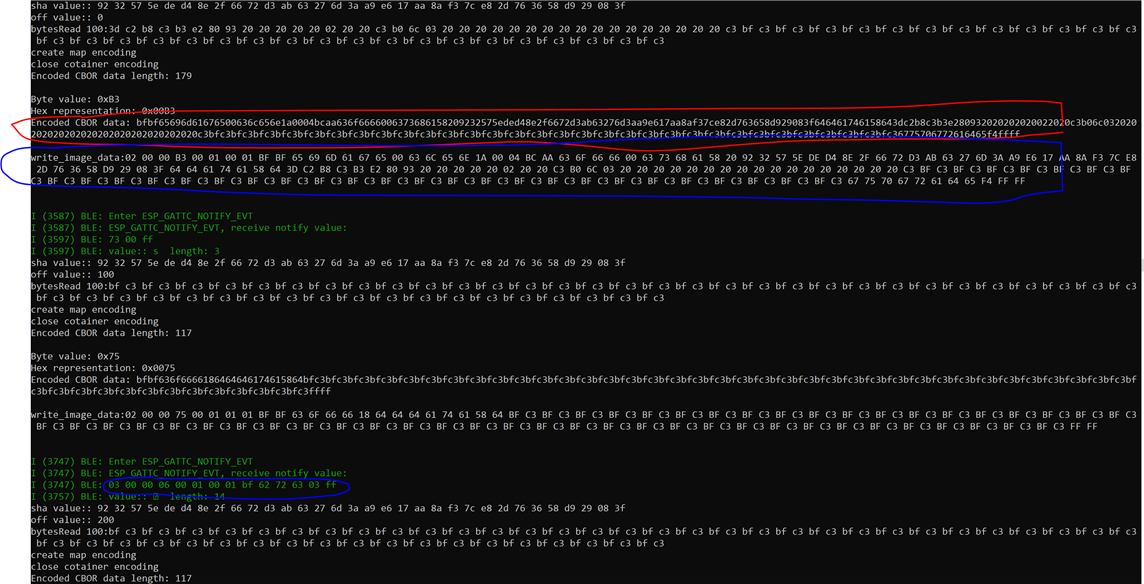
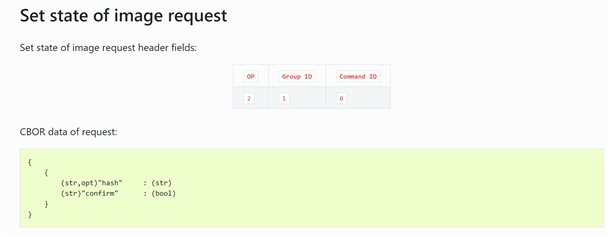
Now, I tried to send the command to set the state of image to find out the format expected for the commands as its CBOR data is in a similar format with two brackets.
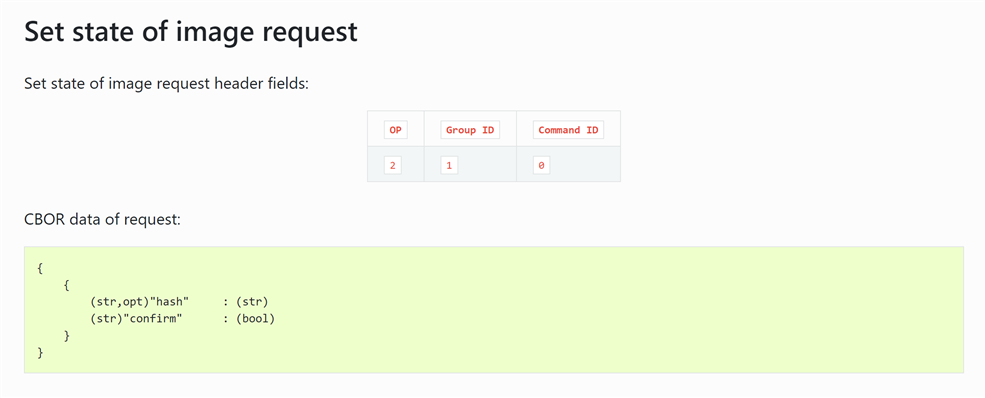
I tried sending in the format as shown on the webpage with only the compulsory field of confirm, just to see if I get a response. No matter what combination(single bracket, two bracket) I try it gives an error when I just send the confirmation field value in CBOR data.