Hi,
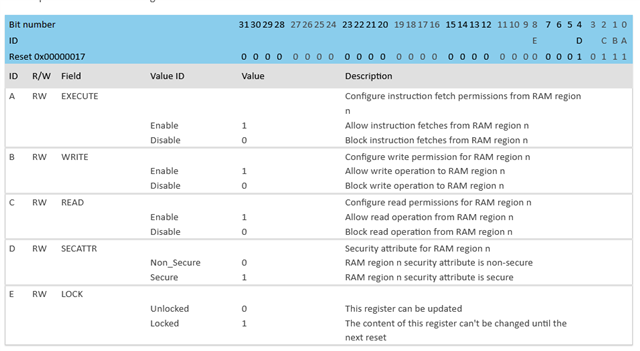
I'd like to have a memory region with some data that should only be written by some special functions, but can be read by the whole system.
This is to make sure that no bugs in other parts can accidentally corrupt this data. In previous projects on STMs I achieved this by using the MPU and a priviledged mode to write.
What is the recommended way to do this with Nordic Connect SDK / Zephyr RTOS on the nRF5340?
I saw that using the User mode can do that, but this adds a lot of overhead to system calls and is probably not the right choice.
Best regards,
Lars