Hello,
I've recently purchased nRF 52840 dongle (Just a beginner). Installed nRF Connect desktop app on macbook pro. My goal is to sniff BLE frames in wireshark.
To do so, I have followed the user guide "nRF Sniffer for Bluetooth LE" v4.1.0. Everything has worked out fine. I am able to see random LE packets in wireshark.
Now, I want to capture packets between my iphone 11 pro and ipod. As far as I know they should be working on BLE (please correct me if wrong). While I listen to a song over this channel, I start the Wireshark to sniff, and get the result as depicted in the picture.
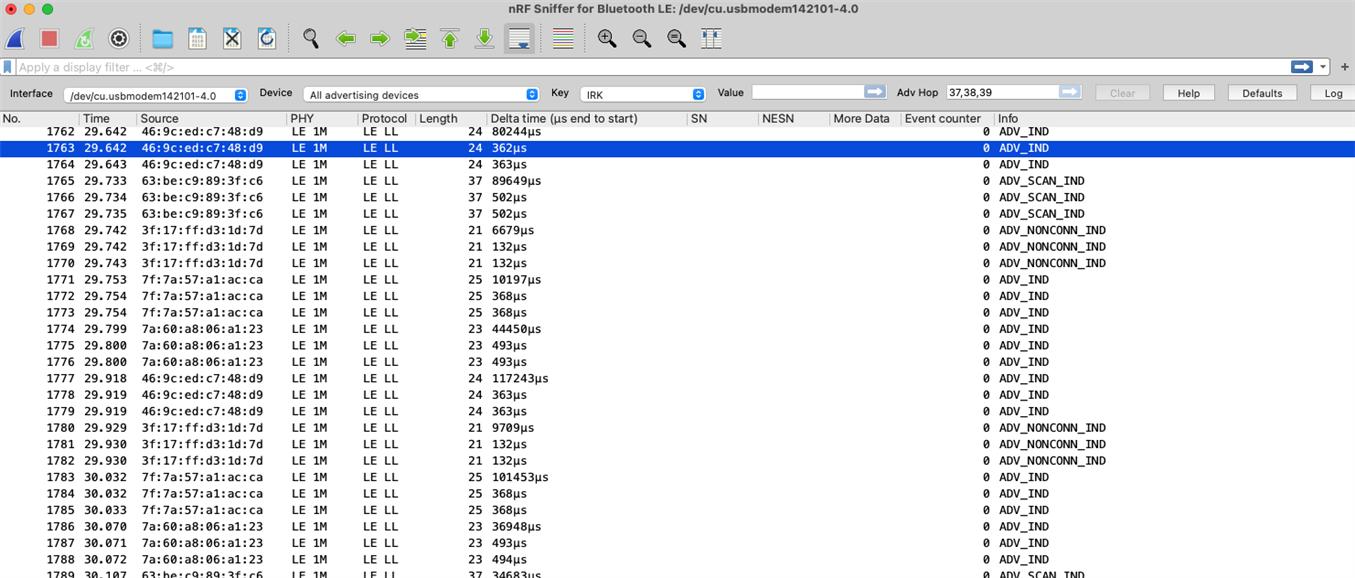
As you can see, all the packets captured are of advertisements. And I am unable to see any data packets (scrolled all way down). Can you please guide me on how to capture all packets advertisement as well as data ? Is there a default configuration that is filtering out the data packets that I should disable ?


