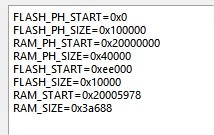
Hi
I am working with the SDK secure bootloader from the SDK 17.1.0. The generated encrypted zip package we transfer with DFU and the APP and this is working great. The application image is too big to use the dual image feature. We have an external flash connected with QSPI and already implemented the possibility to receive and store the same zip package in this external QSPI flash.
Now we have to change the secure bootloader to read the new zip file content from this external flash in the bootloader and not over the BLE DFU feature. To get this feature, I checked the QSPI_booloader project in the examples folder (examples\peripheral\qspi_bootloader\pca10056\blank\ses) but can't see where this project is using the bootloader features like to check the CRC, the crypto key and all other features like in the secure bootloader project. Or is the idea to use this project to implement the start address to the existing secure bootloader project and this code will start reading from the external flash instead of the received files from the BLE DFU connection?
Is there an existing sample how to implement this feature in the secure bootloader project?
Thanks a lot for inputs, Dominik