Note. This issue only occurs if using the Nordic Soft Device controller or the Packetcraft controller.
I am working with the nRF5340 audio development boards.
I have a project with a central device (used as a Broadcast Assistant) and a peripheral device (used as an audio broadcast receiver). They both form an ACL connection and exchange data.
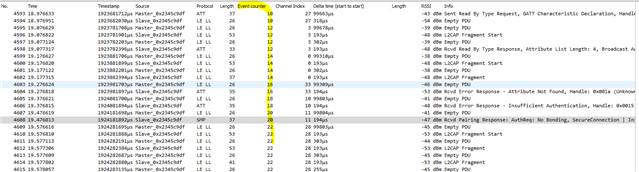
Whenever the receiver is syncing to a broadcast source and it gets disconnected from the central for whatever reason, the central manages to re-connect to the peripheral, however the BASS discovery fails with BT_HCI_ERR_INSUFFICIENT_SECURITY. The following error is displayed : <wrn> bt_gatt: gatt_exchange_mtu_func: conn 0x200018c8 err 0x0e
.
The only way to solve this is by rebooting the receiver / peripheral.
For both the central and receiver applications, bonding is disabled in the proj.conf as follows :
CONFIG_BT_BONDABLE=n
In that case, I can't understand why the BASS re-discovery would fail due to a security error error.
As mentioned above. This only happens when using the Nordic Soft Device controller or the Packetcraft controller. Using the Zephyr controller, the re-discovery works fine without this security problem.
How can there be this security issue only when using those two controllers, and by using the Zephyr controller with the exact same configuration (bonding disabled etc.) it is fine?
Below are the logs from my central application when it re-connects. Thanks in advance for any help or suggestions.
Disconnected from device EE:0B:7C:30:59:12 (random) (reason 0x3e) About to connect to EE:0B:7C:30:59:12 Connection pending.. Successfully connected to device EE:0B:7C:30:59:12 (random) Now discovering.. [00:01:04.517,425] <wrn> bt_gatt: gatt_exchange_mtu_func: conn 0x200018c8 err 0x0e [00:01:04.517,456] <dbg> bt_bap_broadcast_assistant: service_discover_func: Could not discover BASS Error! BASS discover failed (-6)