Hello Nordic Semi,
My Platform: nRF52840 + S140 SoftDevice + Secure Bootloader, SDK base v15.2
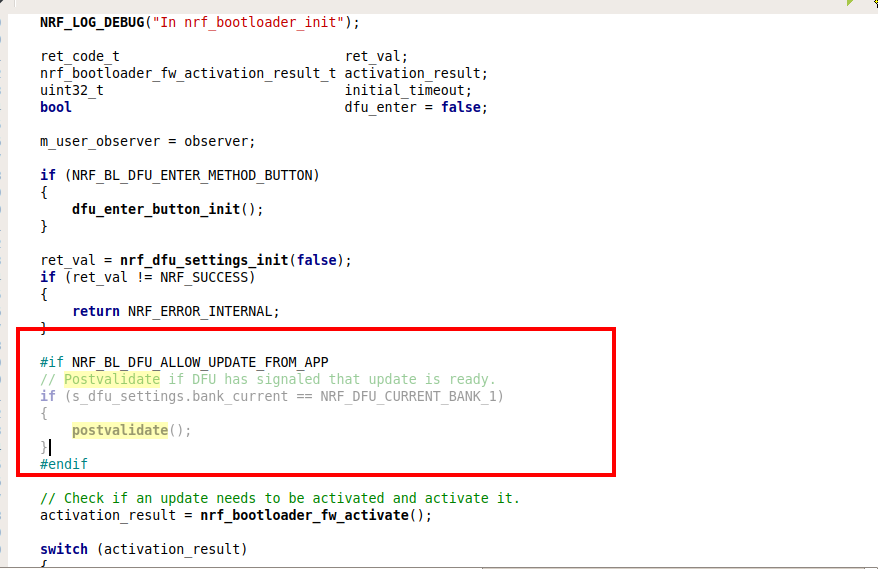
I am working on a project requiring to transport application images to flash without using of the well established DFU/Mobile method. Images are transported via BLE connection during application runtime and written to flash using customized means. Assuming the whole application image is transported and written to free flash space, I need to then prepare the system to boot and run the new image. This requires some coordination with the bootloader settings configuration by the running application before restart.
Question: What are the specific steps necessary to inform/configure the bootloader to boot the newly written image?
- Edwin