Hi,
We are trying to implement Apple Notification Center Service (ANCS) in the custom board, and we came across your implementation.
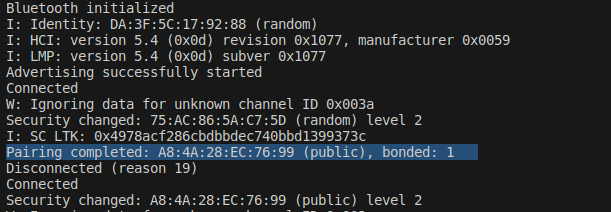
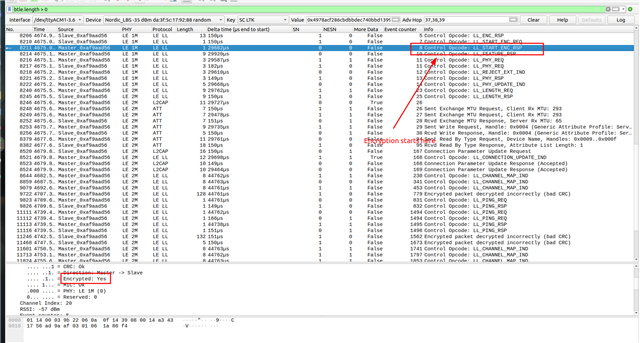
We try to sniff the discovery procedure using Wireshark and we are getting "Encrypted packet decrypted incorrectly (bad MIC)" error in the Wireshark logs.
We started the sniffer from the beginning itself that is, we are sniffing the board before pairing and even then, we are getting the above error message.
Can anyone please guide us to decrypt these packets as it may help us to replicate the procedure on our end too.
We are new to Wireshark tool and sniffer terms so please help us on how to use the Wireshark and submit the passkey to decrypt these packets.