Hello, I'm trying to do the fota via azure IoT hub, except I can't, I don't know if I'm doing it wrong because I followed the doc Azure FOTA https://shorturl.at/fsAJ1 ainsi que Azure IoT Hub https://shorturl.at/eoT57 , maybe I missed something.
sdk 2.5.99-dev1
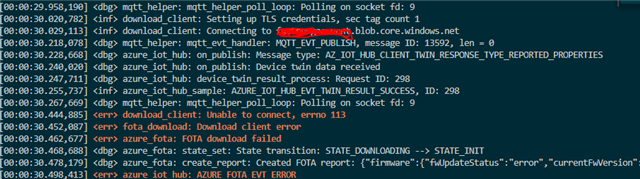
I would like to add this, when try to download the zephyr.bin on my azure
<err> download_client: Unable to connect, errno 113
[00:00:44.678,955] <err> fota_download: Download client error
[00:00:44.689,544] <err> azure_fota: FOTA download failed
If you need more information, I'm open, thank you, I hope to find a solution :)


