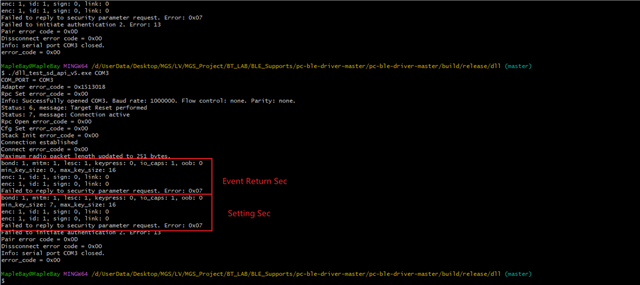
I'm using pc-ble driver-master for programming.
The hardware uses 52840 dongle and calls SD_API_V5.
After I successfully connected, I sent a pairing request using the sd_ble_gap_authenticate() function, The sd_ble_gap_sec_params_reply() function is then used in the "BLE_GAP_EVT_SEC_PARAMS_REQUEST" event.
But this function has an error message 0x07, I try to check or use other parameters to reply will get an error.