Hi,
We have a project where we are using TF-M application along with DFU and we observe a memory overflow in the TF-M partition when we try to reduce the TF-M partition size.
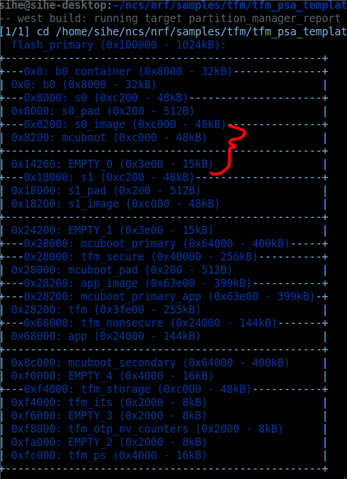
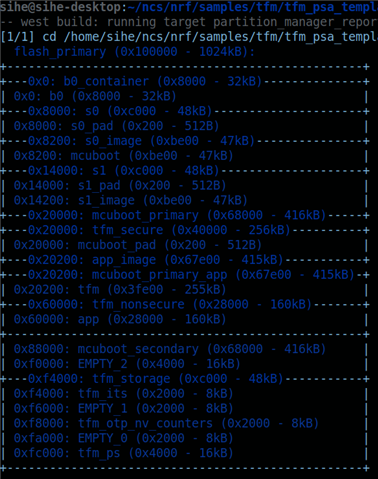
Attached the memory report.
What is b0 partition and EMPTY_X partitions are used? How to reduce these partitions size?
We see TF-M is consuming around 270KB and how to reduce this partition at least to its half.
We basically need the TF-M partition to be minimal to make room for application in non-secure partition.