Hi,
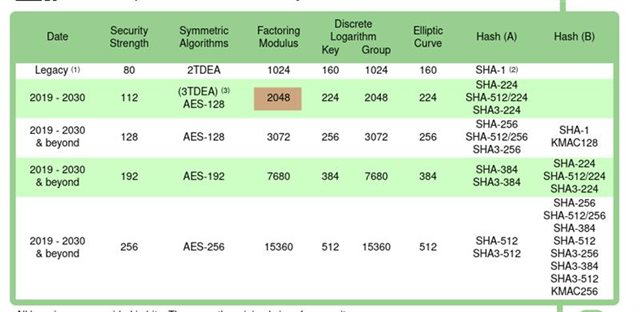
The RSA crypto sample from the 2.5.0 SDK fails at psa_generate_key() returning -134. The sample is by default configured to use 2048-bit keys.
Note that, It fails with the same error code also when changing the sample code and configuration to use say for example - changing it to CONFIG_PSA_WANT_RSA_KEY_SIZE_1536=y or configuring CONFIG_PSA_WANT_RSA_KEY_SIZE_1024=y.
Please note, the AES samples and the ECDH samples from the 2.5.0 SDK works very well on this board. I don't understand why the RSA sample application fails with the UNSUPPORTED error code.
(1) When can the basic/default RSA sample application in SDK 2.5.0 fail on the nRF5340 Development Kit?
(2) We intend to use PSA API for RSA OAEP with key size CONFIG_PSA_WANT_RSA_KEY_SIZE_3072. Is this supported in SDK 2.5.0?
Thanks,
Mathi.
#PSA #Crypto #RSA #SDK 2.5.0 #SAMPLE#nRF5340 DK #keyformat#keygeneration #openssl-versus-PSA