Hello,
I'm currently debugging an issue we are having with MQTT device shadow interaction on the nrf9160. The issue presents when we push a large amount of config JSON to the device shadow. This typically happens when we are setting up a new device for the first time and need to set all the parameters in the "config" object via the REST API. The issue is when this large delta occurs the device will try and sync it via MQTT and it gets stuck in a connect/disconnect loop.
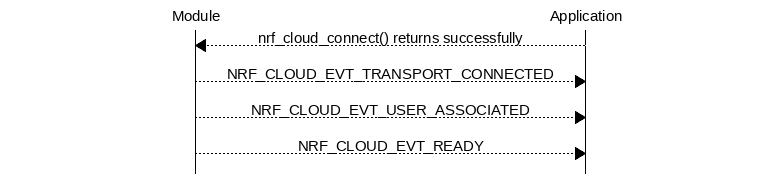
I'm currently looking at once specific case that I can get to repeat multiple times. Where the following events occur in sequence:
1. NRF_CLOUD_EVT_TRANSPORT_CONNECTED occurs
2. NRF_CLOUD_EVT_RX_DATA_SHADOW occurs with the large delta (in my case about 1.3Kb)
3. NRF_CLOUD_EVT_USER_ASSOCIATED occurs
4. NRF_CLOUD_EVT_TRANSPORT_DISCONNECTED occurs for reason -> NRF_CLOUD_DISCONNECT_MISC
5. The LTE connection is reset (not a reboot) and it attempts to connect again and goes through the same sequence.
Now the device never gets a chance to send the shadow delta back up to the cloud because our firmware waits until NRF_CLOUD_EVT_READY before we send any data back to nrfCloud. And because we don't acknowledge the shadow delta it gets sent again the next time we connect, resulting in an endless loop.
The question that comes to mind is why we are getting shadow data before receiving, NRF_CLOUD_EVT_READY? The documentation here seems to imply this shouldn't happen?
Any insight on how to debug this further would be greatly appreciated.
Thanks!

