Hi,
I am currently working with the nRF9160DK board, using SDK version 2.5.1, and I have encountered an issue regarding connectivity to the AWS IoT cloud.
I have successfully connected my board to MQTT and have been able to publish and subscribe to topics using a regular SIM card with a data pack,so I confirmed that internet connection is done. However, when attempting to connect to AWS IoT using the same SIM card in the provided sample code, I am experiencing connectivity issues.
I have ensured that I configured all necessary parameters in the sample code given, including:
- CONFIG_AWS_IOT_BROKER_HOST_NAME
- CONFIG_MQTT_HELPER_SEC_TAG
- CONFIG_AWS_IOT_CLIENT_ID_STATIC
Despite this, I am not receiving the expected output,
After flashing the sample, we can receive those two lines in the image. I'm not getting the remaining lines.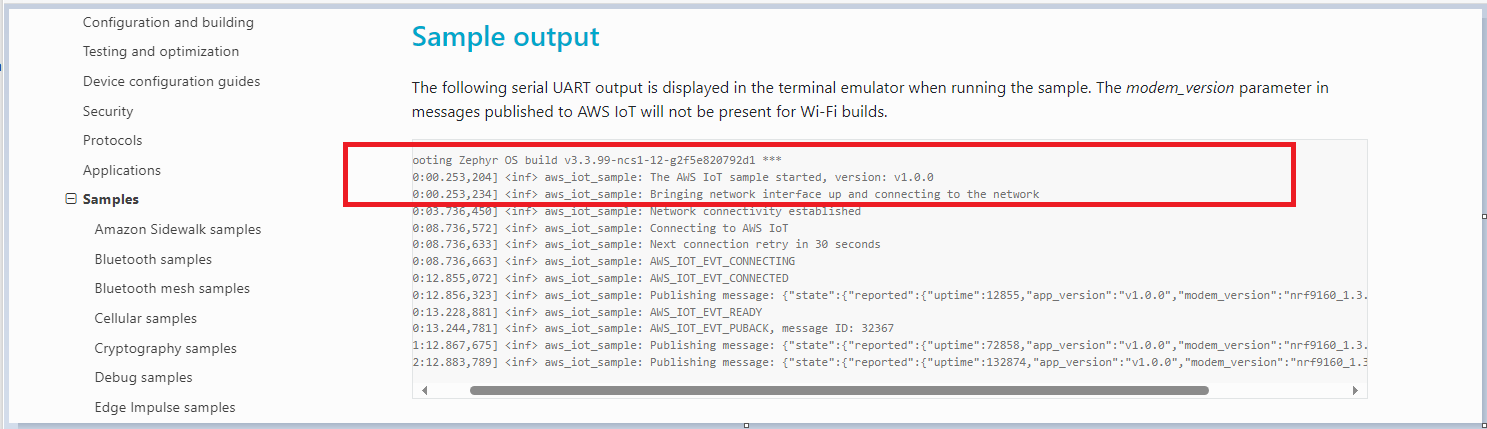
and I'm uncertain whether the SIM card compatibility could be a factor, or if there might be an issue with my code implementation.
Could you please provide guidance on whether an IoT-specific SIM card (LTE-M or NB-IoT) is required for connecting to AWS IoT? Additionally, I would appreciate any insights or troubleshooting tips you may have regarding this connectivity issue.
Thank you in advance for your assistance.