Hi,
I was trying to decrypt an encrypted message I send form my phone using the psa/crypto library. I managed to send the encrypted message over to my board by ble correctly, however when I tried to decrypt the message, I was meet with an error (status -135). I was unable to find any information with regards to this error code. The picture below explains my issue:
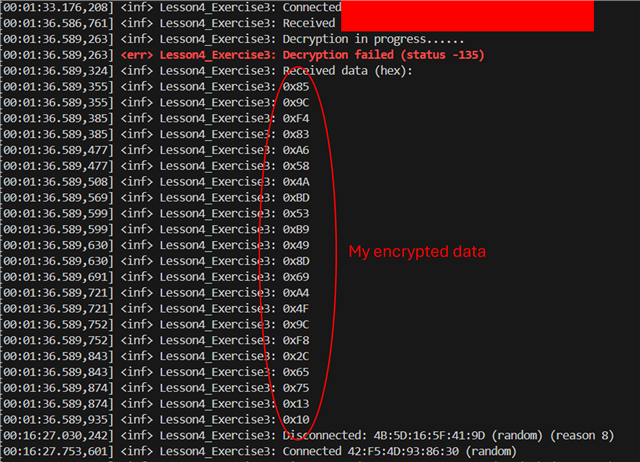
As seen from the image, I am able to send the encrypted data from my phone correctly to the board but I am unable decrypt it. I am quite sure I have implemented the decryption process correctly as I did not run into the error log I have set for debugging until the decryption process. Below is the segment of the code I wrote for the decryption:
final nonce = Uint8List.fromList([0x10, 0x11, 0x12, 0x13, 0x14, 0x15, 0x16, 0x17, 0x18, 0x19, 0x1A, 0x1B]);
final aad = Uint8List.fromList([0x00, 0x01, 0x02, 0x03, 0x04, 0x05, 0x06, 0x07]);


