Hi guys,
We are building an IoT device on nRF9160
The main protocol is MQTT and we are using AWS IoT Core as a Cloud provider.
MQTT client is based on nRF Connect SDK 2.5.0 mqtt_helper library.
We want to use AWS Device Adviser (https://docs.aws.amazon.com/iot/latest/developerguide/device-advisor.html) in our tests.
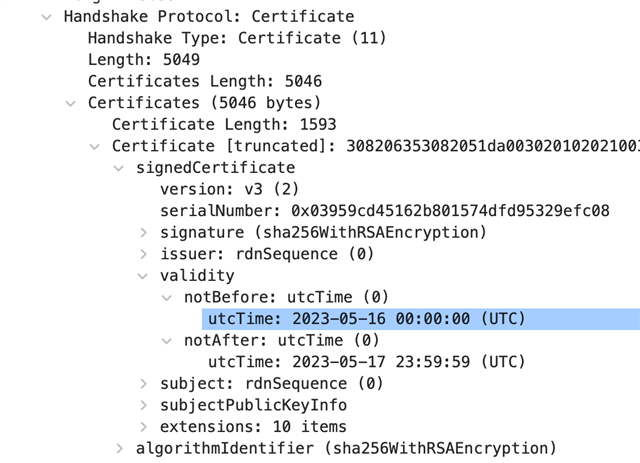
Most of the supported tests are green, but we are facing a problem with TLS Expired Server Certificate test (https://docs.aws.amazon.com/iot/latest/developerguide/device-advisor-tests-tls.html#expired-server) The test always fails, that means the device can connect to a server with an expired certificate.
I've attached the test log from AWS Device Adviser
Any thoughts on what can be wrong? Missed config options?
BR,
Alexey