We have some custom hardware that utilises an NRF52832. Up until recently, all our firmware was built on NCS V2.2.0, which I believe used Zephyr V3.2.99. We have implemented DFU for firmware upgrades, and haven't had any issues with this. Up until now.
The latest version of our firmware has been built around NCS V2.6.0, which I think uses Zephyr V3.5.99. There were a bunch of CONFIG setting changes that I need to make in the transition from NCS V2.2.0 to NCS V2.6.0 associated with setting up the DFU functionality.
We have a custom App that we can use for customers to complete a firmware upgrade. That initiates the transfer of the new image file into the spare slot, resets the device at the completion, and then awaits a response from the SMP service (the App has subscribed to the SMP Service notifications) to tell it that the new image has been accepted and the device has booted up using the new image.
For whatever reason, that notification from the device to the App via the SMP service is no longer occurring, so our App sits there endlessly waiting.
When we try and test the same functionality using Nordic's Device Manager App, we see the following:
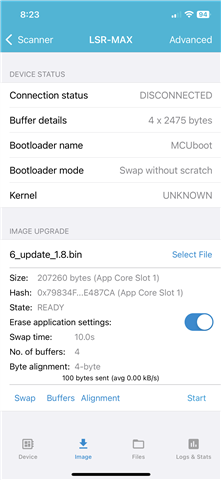
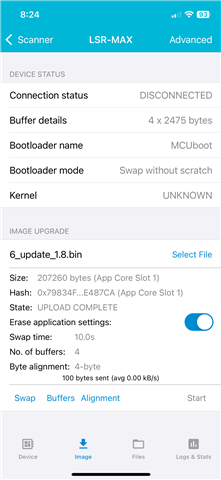
- New image uploads into Slot 1 OK
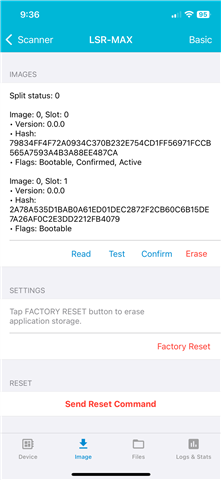
- READ - this confirms the old image in Slot 0 and the new, pending image, in Slot 1
- TEST - this confirms the new image in Slot 1 as the one to boot up from next time the device starts up
- RESET - this works as expected
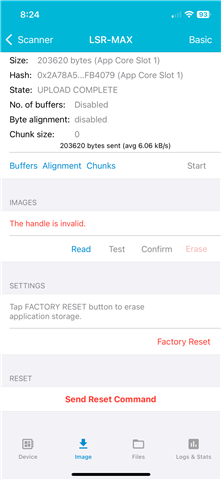
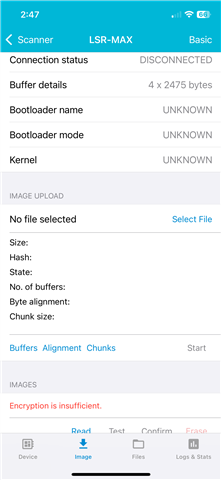
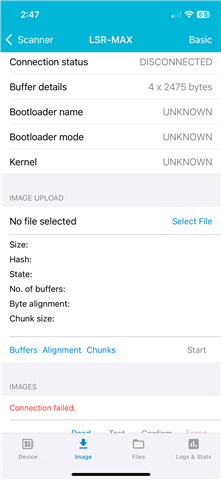
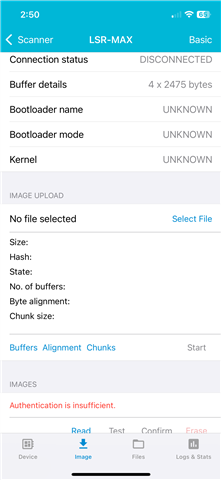
- CONFIRM - this fails, with either an error message that says "Insufficient handle" or something about insufficent authentication
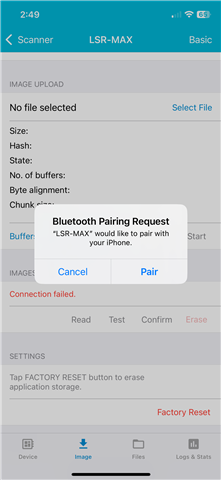
Basically, it looks like pairing/bonding information is getting wiped in the DFU process. But this authentication either wasn't needed when we were doing DFU with V2.2.0, or the pairing/bonding info wasn't getting erased with the new image upload.
I suspect there is some CONFIG setting that is now being set that previously wasn't. I've attached my proj.conf file so you can see how I currently have things configured
# Operational CONFIG settings # General CONFIG_REBOOT=y CONFIG_GPIO=y CONFIG_BOARD_ENABLE_DCDC=n CONFIG_ADC=y # Logging CONFIG_LOG=y CONFIG_LOG_MODE_MINIMAL=n CONFIG_LOG_DEFAULT_LEVEL=0 # Boot CONFIG_BOOT_BANNER=n #Device Name - will be visible to clients scanning CONFIG_BT_DEVICE_NAME="My Device" # Bluetooth CONFIG_BT=y CONFIG_BT_PERIPHERAL=y CONFIG_BT_SMP=y CONFIG_BT_GATT_CLIENT=y CONFIG_BT_GATT_DM=y CONFIG_BT_MAX_PAIRED=10 CONFIG_BT_ID_MAX=10 CONFIG_BT_ID_UNPAIR_MATCHING_BONDS=y CONFIG_BT_KEYS_OVERWRITE_OLDEST=y CONFIG_BT_SMP_SC_PAIR_ONLY=y #CONFIG_BT_CTS_CLIENT=y #PHY update needed for updating PHY request CONFIG_BT_USER_PHY_UPDATE=y #For data length update CONFIG_BT_USER_DATA_LEN_UPDATE=y CONFIG_BT_BUF_ACL_TX_COUNT=10 CONFIG_BT_ATT_PREPARE_COUNT=2 # Enable CTS client CONFIG_BT_CTS_CLIENT=y # Below is setup to let DIS information be read from settings CONFIG_BT_SETTINGS=y CONFIG_SETTINGS_RUNTIME=y CONFIG_SETTINGS=y #Enable MCUBOOT bootloader build in the application CONFIG_BOOTLOADER_MCUBOOT=y #Include MCUMGR and the dependencies in the build CONFIG_NCS_SAMPLE_MCUMGR_BT_OTA_DFU=y CONFIG_NCS_SAMPLE_MCUMGR_BT_OTA_DFU_SPEEDUP=y CONFIG_NCS_SAMPLE_MCUMGR_BT_OTA_DFU_VALIDATION=y # Set stack and heap sizes CONFIG_MAIN_STACK_SIZE=2048 CONFIG_HEAP_MEM_POOL_SIZE=2048 # Allow flash CONFIG_FLASH=y CONFIG_FLASH_PAGE_LAYOUT=y CONFIG_FLASH_MAP=y CONFIG_NVS=y CONFIG_MPU_ALLOW_FLASH_WRITE=y # Enable Power Management CONFIG_POWEROFF=y # Required to disable default behavior of deep sleep on timeout CONFIG_PM_DEVICE=y # Enable I2C CONFIG_I2C=y CONFIG_COUNTER=y CONFIG_PCF85063A=y #cJSON CONFIG_CJSON_LIB=y CONFIG_NEWLIB_LIBC=y CONFIG_NEWLIB_LIBC_FLOAT_PRINTF=y # Sensors CONFIG_SENSOR=y # CONFIG below here set up to minimise flash usage # Disable features not needed CONFIG_TIMESLICING=n CONFIG_ASSERT=n # Disable Bluetooth features not needed CONFIG_BT_DEBUG_NONE=y CONFIG_BT_ASSERT=n CONFIG_BT_GATT_CACHING=n CONFIG_BT_SETTINGS_CCC_LAZY_LOADING=y CONFIG_BT_HCI_VS_EXT=n # Disable Bluetooth controller features not needed CONFIG_BT_CTLR_PRIVACY=n CONFIG_BT_CTLR_PHY_2M=n # Reduce Bluetooth buffers CONFIG_BT_BUF_EVT_DISCARDABLE_COUNT=1 CONFIG_BT_BUF_EVT_RX_COUNT=2 # Drivers and peripherals CONFIG_WATCHDOG=n CONFIG_SPI=n # Interrupts CONFIG_DYNAMIC_INTERRUPTS=n # Memory protection CONFIG_THREAD_STACK_INFO=n CONFIG_THREAD_CUSTOM_DATA=n CONFIG_FPU=n # Console CONFIG_EARLY_CONSOLE=n # Build CONFIG_SIZE_OPTIMIZATIONS=y
Can anyone assist me in resolving this issue? We need to roll out the updated version of firmware, but can't until we can ensure a smooth upgrade process through our App.
Regards,
Mike