hi support team,
1. customer asks about one question about hash in our dfu init packet.
our dfu lib will send init packet to our 52 device, how to use this hash in init.data in our bootloader project.
2. and another question is what's the meaning of this hash as below,
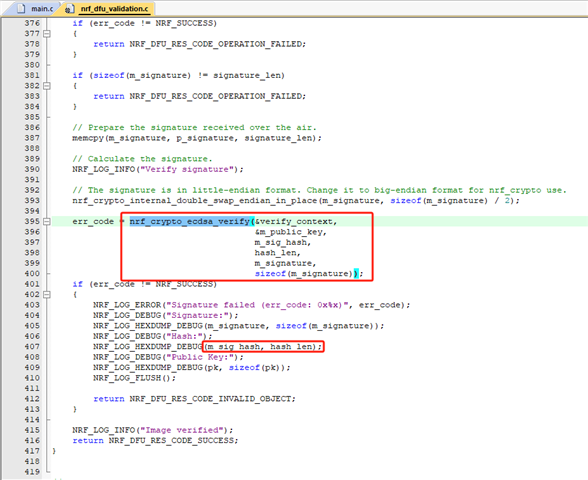
Regards,
William.

