Hi,
I'm working on nRF5340, NCS v2.6.1, Zephyr v3.4.99.
The net core is running the child image HCI RPMsg controller.
Th app core is running application and child image mcuboot.
I know that by default MCUboot uses generated NSIB key pair <ncs>/bootloader/mcuboot/root-rsa-2048.pem, not to be used for production.
Therefore, for production, my goal is to hash and sign image using custom keys and let MCUBoot to validate it at boot time.
Generating the key was pretty simple using
$ ./scripts/imgtool.py keygen -k mycompany.pem -t rsa-2048
Then I put the key file at path /home/gabriele/myproject/mycompany.pem
In myproject/child_image/mcuboot.conf I set
CONFIG_BOOT_SIGNATURE_KEY_FILE="/home/gabriele/myproject/mycompany.pem"
CONFIG_BOOT_SIGNATURE_TYPE_RSA=y
CONFIG_BOOT_VALIDATE_SLOT0=y
In /home/gabriele/myproject/prj.conf I set
CONFIG_SECURE_BOOT=y
CONFIG_SB_SIGNING_KEY_FILE="/home/gabriele/myproject/mycompany.pem"
At build time I get the following error in the end
[153/158] Linking C executable zephyr/zephyr_pre0.elf
[154/158] Generating linker.cmd
[155/158] Generating isr_tables.c, isr_tables_vt.ld, isr_tables_swi.ld
[156/158] Building C object zephyr/CMakeFiles/zephyr_final.dir/misc/empty_file.c.obj
[157/158] Building C object zephyr/CMakeFiles/zephyr_final.dir/isr_tables.c.obj
[158/158] Linking C executable zephyr/zephyr.elf
Memory region Used Size Region Size %age Used
FLASH: 24538 B 34176 B 71.80%
RAM: 3488 B 64 KB 5.32%
SRAM1: 0 GB 64 KB 0.00%
IDT_LIST: 0 GB 32 KB 0.00%
[232/243] Building C object zephyr/CMakeFiles/zephyr_final.dir/isr_tables.c.obj
[233/243] Creating public key from private key used for signing
[235/243] Completed 'b0n_subimage'
[236/243] Creating data to be provisioned to the Bootloader, storing to provision.hex
[238/243] Generating zephyr/b0n_container.hex
[239/243] Linking C executable zephyr/zephyr.elf
Memory region Used Size Region Size %age Used
FLASH: 177528 B 222 KB 78.09%
RAM: 47604 B 64 KB 72.64%
SRAM1: 0 GB 64 KB 0.00%
IDT_LIST: 0 GB 32 KB 0.00%
[240/243] Generating zephyr/app.hex
[240/243] Creating signature of application
[241/243] Creating validation for zephyr.hex, storing to
[243/243] Generating zephyr/merged_CPUNET.hex
[368/394] Building C object zephyr/CMakeFiles/zephyr_final.dir/isr_tables.c.obj
[369/394] Creating data to be provisioned to the Bootloader, storing to provision.hex
Traceback (most recent call last):
File "/home/gabriele/spiro-dev/nrf53sdk/ncs/zephyr/../nrf/scripts/bootloader/provision.py", line 199, in <module>
main()
File "/home/gabriele/spiro-dev/nrf53sdk/ncs/zephyr/../nrf/scripts/bootloader/provision.py", line 180, in main
hashes = get_hashes(
File "/home/gabriele/spiro-dev/nrf53sdk/ncs/zephyr/../nrf/scripts/bootloader/provision.py", line 140, in get_hashes
digest = sha256(VerifyingKey.from_pem(f.read()).to_string()).digest()[:16]
File "/home/gabriele/spiro-dev/nrf53sdk/zephyr/python-env/lib/python3.8/site-packages/ecdsa/keys.py", line 318, in from_pem
return cls.from_der(
File "/home/gabriele/spiro-dev/nrf53sdk/zephyr/python-env/lib/python3.8/site-packages/ecdsa/keys.py", line 393, in from_der
raise der.UnexpectedDER(
ecdsa.der.UnexpectedDER: Unexpected object identifier in DER encoding: (1, 2, 840, 113549, 1, 1, 1)
[371/394] Completed 'hci_ipc_subimage'
FAILED: zephyr/provision.hex /home/gabriele/spiro-dev/apps/spiro/build/zephyr/provision.hex
cd /home/gabriele/spiro-dev/apps/spiro/build/zephyr && /home/gabriele/spiro-dev/nrf53sdk/zephyr/python-env/bin/python /home/gabriele/spiro-dev/nrf53sdk/ncs/zephyr/../nrf/scripts/bootloader/provision.py --s0-addr 0x14200 --s1-addr 0x68100 --provision-addr 0xff8100 --public-key-files /home/gabriele/spiro-dev/apps/spiro/build/zephyr/nrf/subsys/bootloader/generated/public.pem --output /home/gabriele/spiro-dev/apps/spiro/build/zephyr/provision.hex --max-size 0x280 --num-counter-slots-version 20
[373/394] Generating ../../zephyr/net_core_app_update.bin
image.py: sign the payload
[374/394] Linking C executable zephyr/zephyr.elf
Memory region Used Size Region Size %age Used
FLASH: 320356 B 343808 B 93.18%
RAM: 229084 B 440 KB 50.84%
IDT_LIST: 0 GB 32 KB 0.00%
[375/394] Generating ../../zephyr/net_core_app_signed.hex
image.py: sign the payload
ninja: build stopped: subcommand failed.
Can anyone give a help ?

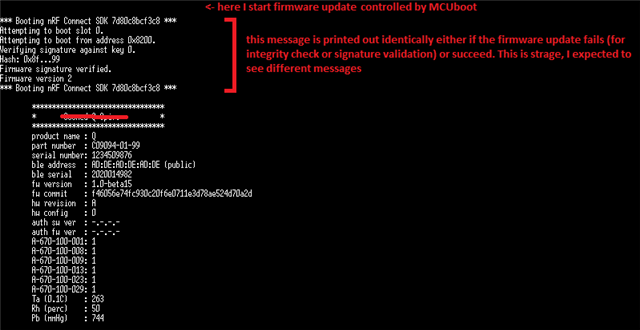
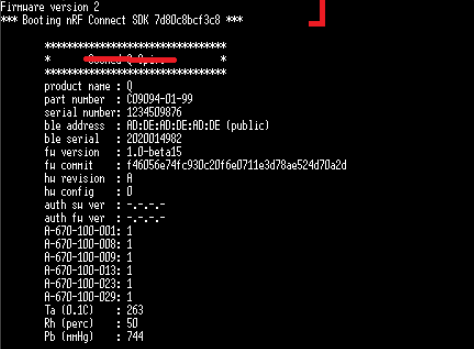 ?
?