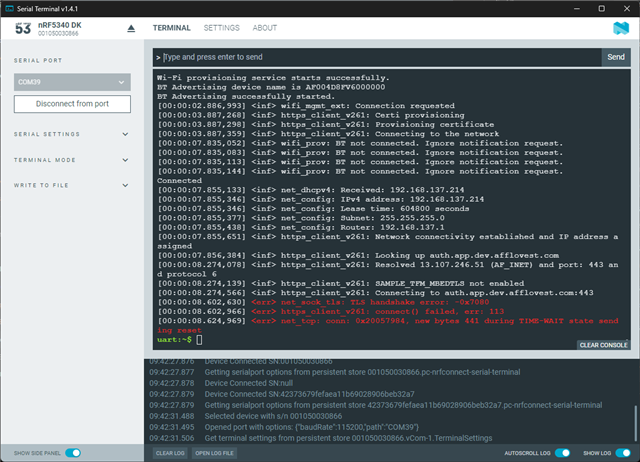
With nRF7002DK and TF-M (nrf7002dk_nrf5340_cpuapp_ns.conf) configuration, the sample project works for example.com:
*** Booting nRF Connect SDK v3.5.99-ncs1-1 ***
HTTPS client sample started
Bringing network interface up
Provisioning certificate
Connecting to the network
[00:00:04.949,981] <inf> wifi_mgmt_ext: Connection requested
[00:00:09.183,044] <inf> net_dhcpv4: Received: 192.168.101.16
Network connectivity established and IP address assigned
Looking up example.com
Resolved 93.184.215.14 (AF_INET)
Connecting to example.com:443
Sent 61 bytes
Received 377 bytes
> HTTP/1.1 200 OK
Finished, closing socket.
Network connectivity lost
Disconnected from the network
However, replace the host with google.com and its associated CA:
[00:00:45.647,186] <inf> wifi_mgmt_ext: Connection requested
[00:00:49.878,845] <inf> net_dhcpv4: Received: 192.168.101.16
Network connectivity established and IP address assigned
Looking up google.com
Resolved 142.250.191.206 (AF_INET)
Connecting to google.com:443
connect() failed, err (22): Invalid argument
Network connectivity lost
Disconnected from the network