I am following the steps to configure the Bluetooth BE Sniffer in Wireshark, but I am having difficulties. I tried both on Windows and Untuntu (Linux).
Setting up nRF Sniffer for Bluetooth LE - Nordic Developer Academy (nordicsemi.com)
Nordic Semiconductor Infocenter
I installed the requirements (pyserial >= 3.5 and psutil)
I put the files indicated in the tutorial in the "Global Extcap path"
I refresh Wireshark (Capture > Refresh Interfaces or pressing F5)
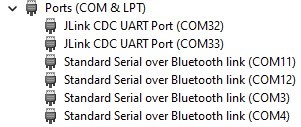
But the nRF hardware interface does not appear as an option in Wireshark.