Hello Nordic Semiconductor tech support team,
HW : nRF52840 ( Build code : nRF52840-CKAA-F )
SW : ncs 2.6.0
Sample Application : zephyr/samples/bluetooth/hci_spi sample with SoftDevice Controller
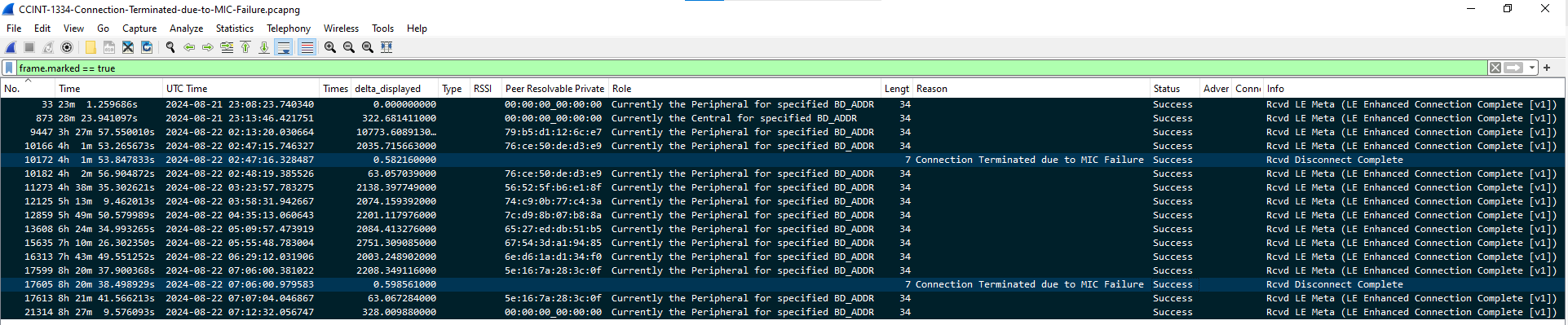
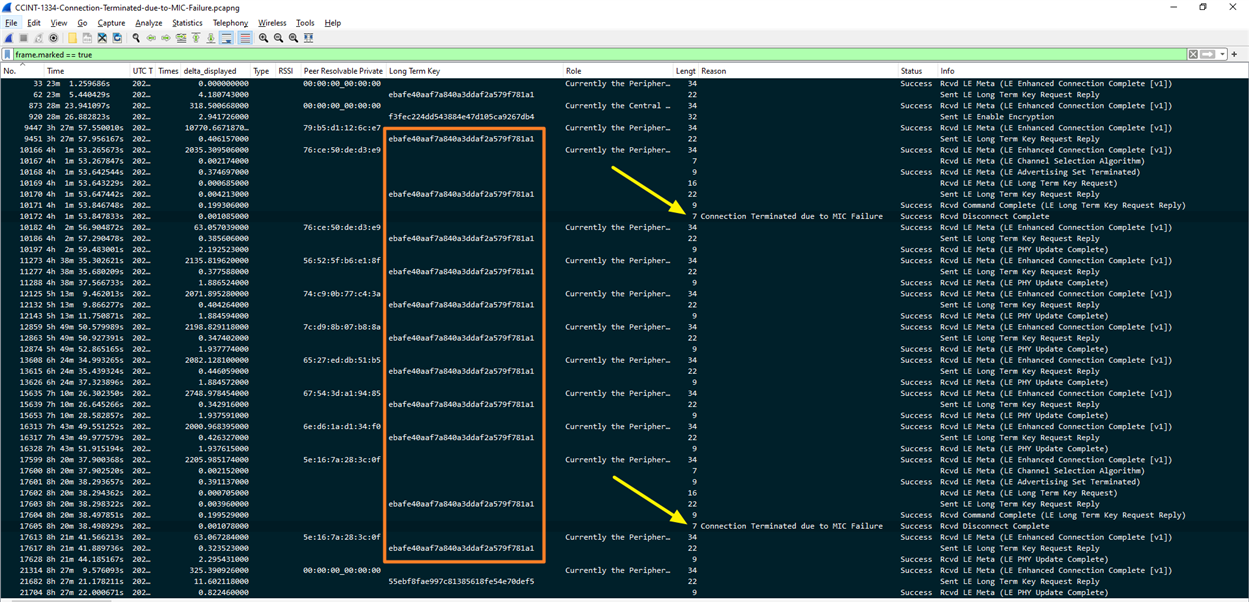
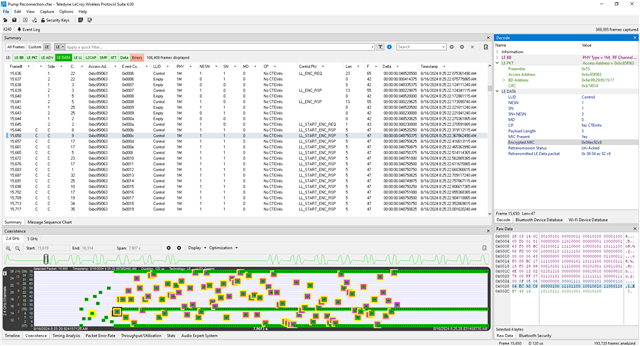
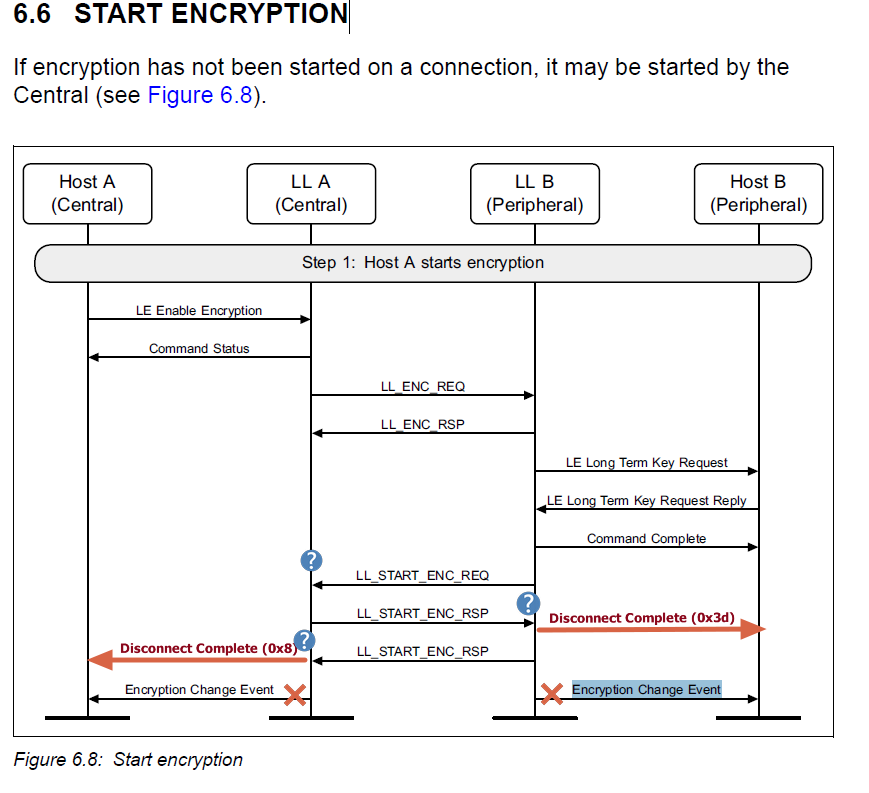
While verifying our software design, we frequently encounter connection errors. Could you help us identify the possible cause of this issue and suggest a resolution? Right after the enhanced connection is completed, we’re expecting an Encryption Change Event from the SoftDevice Controller. However, instead of an Encryption Change Event, a Disconnect Complete (0x05) occurs with the reason ‘Connection Terminated due to MIC Failure (0x3d).
Device A : Android Mobile Phone (central), (iOS case is also reported)
Device B: nRF52840 (Peripheral)
Frame 17605: 7 bytes on wire (56 bits), 7 bytes captured (56 bits) on interface Fake IF, Import from Hex Dump, id 0 (inbound)
Bluetooth
Bluetooth HCI H4
Bluetooth HCI Event - Disconnect Complete
Event Code: Disconnect Complete (0x05)
Parameter Total Length: 4
Status: Success (0x00)
Connection Handle: 0x00cd
Reason: Connection Terminated due to MIC Failure (0x3d)
(highlighted marked HCI events)