Hi all,
We have an application which uses both MCUboot and a watchdog timer. This combination seems to be causing issues anytime we attempt a soft reset using sys_reboot or NVIC reset directly.
Our system;
- Custom board using nRF5340
- ncs v2.2.0
When we attempt a soft reset the following happens;
- Device powers down and enters bg_thread_main() in "ncs\v2.2.0\zephyr\kernel\init.c", it doesn't enter our application main()
- Device enters MCUboot
- After sometime the watchdog resets, the device enters MCUboot again
- Finally the device enters bg_thread_main() again, this time our application main() runs successfully
All this is monitored using UART log (shown below).
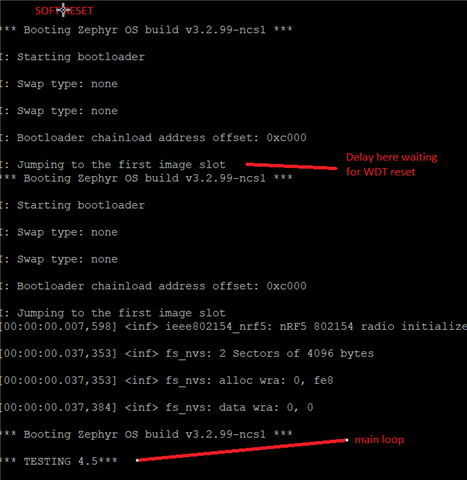
This issue looks similar to another devzone post, however, we've tried the suggestion of adding CONFIG_BOOT_WATCHDOG_FEED to our mcuboot.conf but we still get the same sequence of events.
From the RESET table, software resets don't reset the WDT which explains why we get 2 resets but it doesn't explain why we don't enter our application main loop in 1. We've tried forcing a WDT timer reset instead of a soft reset and this does fix the issue - we only get one reset and it enters our application main loop successfully.
One solution is if we tie a gpio directly to the RESET pin and use this gpio for resets from within the application. This isn't ideal as it requires hardware changes and limits ours design.
Does anyone have any other suggestions we can try?

