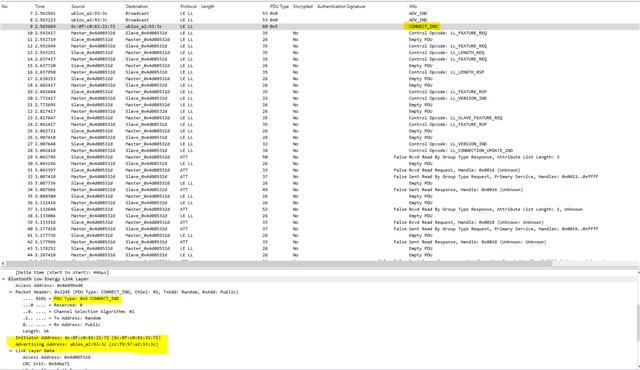
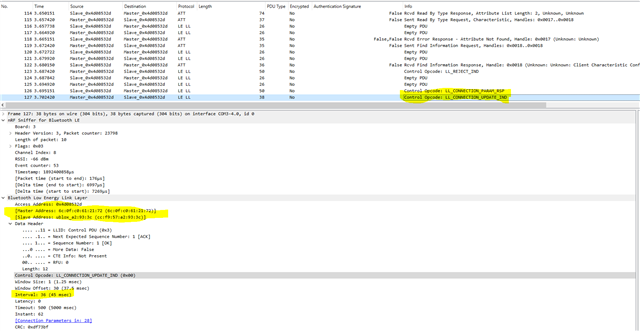
I am using a nrf52840 dongle. I have my own device which has BLE and I am connecting to an app in mobile phone our bluetooth. My goal is to check for the security level what my device has and when it's getting connected with app I was trying to find if there is any security negotiation. To check this I am using the nrf52840 dongle for bluetooth sniffing so that I can check for the security negotiation.
Based on this link I followed all the steps https://academy.nordicsemi.com/courses/bluetooth-low-energy-fundamentals/lessons/lesson-6-bluetooth-le-sniffer/topic/nrf-sniffer-for-bluetooth-le/
I have flashed firmware 4.1.1 version.
I get the PDU type as 0x08
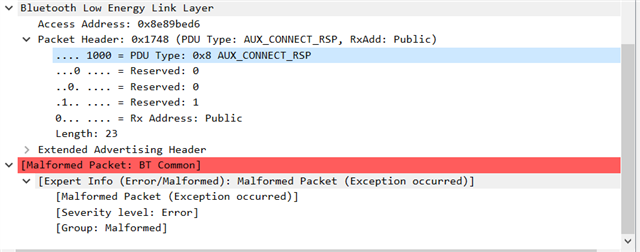
In documentation there is nothing referencing to Packet ID 0x08. It says security level error and CRC is bad wanted to understand more on this.
Also how to check for security level negotiation which packet should I look for specifically? Also with the firmware version 4.1.1 can I get to know the security negotiation?