I know this exact symptoms has been described many other times, and I apologize. However, I carefully searched through all the previously asked questions in merit and could not find a solution to my issue.
Basically it's as follows: I'm trying to reverse-engineer a BLE gadget connected to an Android phone app. I set up the tooling as per the documentation with nrfutil and J-Link;
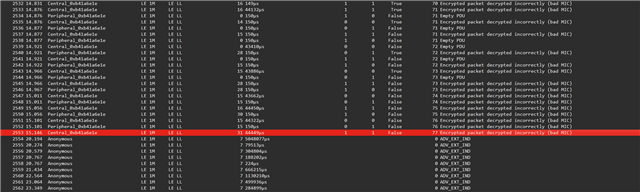
I start the capturing on Wireshark with the Dongle's interface selected, it shows all the BLE traffic around the room as normal. When I start my BLE gadget and select it from the dropdown, it starts capturing the advertisement traffic. I then start the app, with my Bluetooth cache cleared and gadget unpaired, the app attempts to pair with the device and subsequently connect - and here suddenly all ADV / SCAN_REQ / etc. traffic ceases abruptly and no other packet is detected.
If I close the app, the gadget disconnects and immediately resumes the advertisement as if nothing happened.
I have no idea how to proceed from here. From my understanding, in the bare minimum I should at least be able to capture the start of a pairing process? Instead, I get absolutely nothing other than ADV. The logs (both nrfutil.log and the ble-sniffer log) show nothing out of the ordinary.
Any suggestions?
My setup:
- Windows 10
- nRF52840 Dongle flashed with sniffer_nrf52840dongle_nrf52840_4.1.1.zip from .nrfutil\share\nrfutil-ble-sniffer\firmware
- J-Link v7.94i
- nrf-device-lib driver from the pc-nrfconnect-launcher github repository (3 years old?)
- nrfutil 7.13.0 with ble-sniffer 0.13.0 and device 2.6.3
- Wireshark 4.4.1 with the profile import from the nRF Sniffer for Bluetooth LE 4.1.1 starter kit
23:55:52 [INFO] Attempt opening serial port at COM15
23:55:52 [INFO] Subscribing to event DEVICE_ADDED
23:55:52 [INFO] Subscribing to event DEVICE_UPDATED
23:55:52 [INFO] Subscribing to event DEVICE_REMOVED
23:55:52 [INFO] Subscribing to event DEVICES_CLEARED
23:55:52 [INFO] Sending version request
23:55:52 [INFO] Sending ping request
23:55:52 [INFO] Sending timestamp request
23:55:52 [INFO] Sending advertisement hop sequence request for channels [37, 38, 39]
23:55:52 [INFO] Changing state from IDLE to SCANNING
23:55:52 [INFO] Sending scan packet
23:55:52 [INFO] Sending request to use temporary key [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
23:55:52 [INFO] Sending request to clear device list
23:55:52 [INFO] Sniffer statistics: {"packets_sent_by_sniffer":58500,"packets_in_last_connection":null,"connect_event_packet_counter_value":null,"current_connect_request_packet":null,"state":"Idle","last_time":null,"last_timestamp":0}
23:55:52 [INFO] Sniffer statistics: {"packets_sent_by_sniffer":59000,"packets_in_last_connection":null,"connect_event_packet_counter_value":null,"current_connect_request_packet":null,"state":"Idle","last_time":null,"last_timestamp":0}
23:55:52 [INFO] Sniffer statistics: {"packets_sent_by_sniffer":59500,"packets_in_last_connection":null,"connect_event_packet_counter_value":null,"current_connect_request_packet":null,"state":"Idle","last_time":null,"last_timestamp":0}
23:55:52 [INFO] Sniffer statistics: {"packets_sent_by_sniffer":60000,"packets_in_last_connection":null,"connect_event_packet_counter_value":null,"current_connect_request_packet":null,"state":"Idle","last_time":null,"last_timestamp":0}
23:55:52 [INFO] Sniffer statistics: {"packets_sent_by_sniffer":60500,"packets_in_last_connection":null,"connect_event_packet_counter_value":null,"current_connect_request_packet":null,"state":"Idle","last_time":null,"last_timestamp":0}
23:55:52 [INFO] Firmware version 4.1.1
23:55:52 [INFO] Firmware timestamp 2488685752 ms reference:
Oct 10 2024 23:55:52
23:55:52 [INFO] Device with address 71:d5:3f:97:d2:3a random added
23:55:52 [INFO] Device with address 56:3d:97:d:d4:b2 random added
23:55:52 [INFO] Sniffer statistics: {"packets_sent_by_sniffer":61000,"packets_in_last_connection":null,"connect_event_packet_counter_value":null,"current_connect_request_packet":null,"state":"Idle","last_time":"2024-10-10T23:55:52.522909500Z","last_timestamp":2489102376}
23:55:53 [INFO] Device with address eb:f5:eb:4e:75:d7 random added
23:55:54 [INFO] Device with address c:a7:20:45:9a:5e random added
23:55:54 [INFO] Device with address c:a7:20:45:9a:5e public added
23:55:56 [INFO] Device with address 78:2:b7:3:c5:17 public added
23:55:57 [INFO] Device with address 77:1f:e4:3f:26:b4 random added
23:55:59 [INFO] Device with address 56:3d:97:d:d4:b2 public added
23:56:01 [INFO] Device with address a4:93:40:40:0:c1 public added
23:56:04 [INFO] Sniffer statistics: {"packets_sent_by_sniffer":61500,"packets_in_last_connection":null,"connect_event_packet_counter_value":null,"current_connect_request_packet":null,"state":"Idle","last_time":"2024-10-10T23:56:04.595108500Z","last_timestamp":2501174575}
23:56:07 [INFO] Changing state from SCANNING to FOLLOWING
23:56:07 [INFO] Sending follow request to follow device with address a4:93:40:40:0:c1 public
23:56:11 [INFO] Sniffer statistics: {"packets_sent_by_sniffer":62000,"packets_in_last_connection":null,"connect_event_packet_counter_value":null,"current_connect_request_packet":null,"state":"Idle","last_time":"2024-10-10T23:56:11.879048500Z","last_timestamp":2508458515}
23:56:20 [INFO] Sniffer statistics: {"packets_sent_by_sniffer":62500,"packets_in_last_connection":null,"connect_event_packet_counter_value":null,"current_connect_request_packet":null,"state":"Idle","last_time":"2024-10-10T23:56:20.160442500Z","last_timestamp":2516739909}
23:56:49 [INFO] Sniffer statistics: {"packets_sent_by_sniffer":63000,"packets_in_last_connection":null,"connect_event_packet_counter_value":null,"current_connect_request_packet":null,"state":"Idle","last_time":"2024-10-10T23:56:26.274728500Z","last_timestamp":2522854195}
[2024-10-10T23:55:22.453Z] [31864] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-interfaces --extcap-version=4.4 [2024-10-10T23:55:22.728Z] [31752] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-config --extcap-interface COM15-4.4 [2024-10-10T23:55:22.728Z] [8460] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-config --extcap-interface COM1-4.4 [2024-10-10T23:55:22.893Z] [29796] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-dlts --extcap-interface COM1-4.4 [2024-10-10T23:55:22.970Z] [29440] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-dlts --extcap-interface COM15-4.4 [2024-10-10T23:55:51.778Z] [17560] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-config --extcap-interface COM15-4.4 [2024-10-10T23:55:51.849Z] [20596] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-config --extcap-interface COM15-4.4 [2024-10-10T23:55:51.935Z] [31092] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-config --extcap-interface COM15-4.4 [2024-10-10T23:55:52.009Z] [33456] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --capture --extcap-interface COM15-4.4 --fifo \\.\pipe\wireshark_extcap_COM15-4.4_20241011015551 --extcap-control-out \\.\pipe\wireshark_control_ext_to_ws_COM15-4.4_20241011015551 --extcap-control-in \\.\pipe\wireshark_control_ws_to_ext_COM15-4.4_20241011015551 --scan-follow-rsp --scan-follow-aux [2024-10-11T00:31:04.469Z] [25152] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with list [2024-10-11T00:31:37.758Z] [33896] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with version [2024-10-11T00:31:41.955Z] [15328] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with [2024-10-11T00:31:48.859Z] [25416] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with self-upgrade [2024-10-11T00:32:24.333Z] [29524] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-interfaces --extcap-version=4.4 [2024-10-11T00:32:24.612Z] [32152] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-config --extcap-interface COM1-4.4 [2024-10-11T00:32:24.612Z] [20040] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-config --extcap-interface COM15-4.4 [2024-10-11T00:32:24.788Z] [30376] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-dlts --extcap-interface COM1-4.4 [2024-10-11T00:32:24.864Z] [31856] INFO - nrfutil (version = 7.13.0, platform = x86_64-pc-windows-msvc) invoked with ble-sniffer --extcap-dlts --extcap-interface COM15-4.4