Hi Support Team,
I am encountering various problems with the Developer Academy example found here:
1. Unable to debug without GATT errors
To overcome this issue I used logging but:
2. Logging is not working. None of the LOG directives is working
The cause why I need this is:
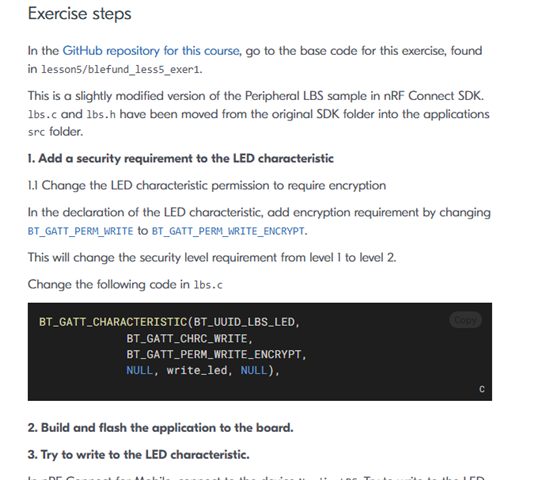
3. I set CONFIG_BT_NUS_SECURITY_ENABLED=y but nothing happend - security is not working
Could you tell me at least how to get the security in the example working?
Also logging is needed
Many thanks in advance.
Regards, Andreas