Hi,
I'm developing on the current setup:
- nRF52840
- Soft Device 140 version 7.2.0
- SDK 17.1.0
- MDK: 8.51
- Segger v4.52c
- Secure bootloader (DFU)
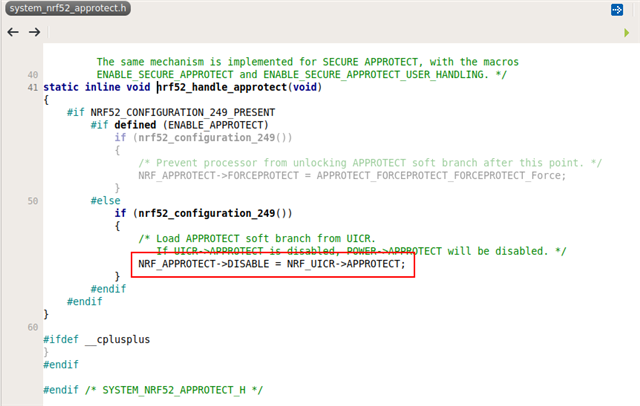
I don't define ENABLE_APPROTECT in the preprocessor and I've followed this guide: Working with the nRF52 Series' improved APPROTECT - Blogs - Nordic Blog - Nordic DevZone, which led me to included this code as the first thing main executes:
void approtect_disable( void )
{
if ( ( NRF_UICR->APPROTECT & UICR_APPROTECT_PALL_Msk ) != ( UICR_APPROTECT_PALL_HwDisabled << UICR_APPROTECT_PALL_Pos ) ) {
NRF_NVMC->CONFIG = NVMC_CONFIG_WEN_Wen;
while ( NRF_NVMC->READY == NVMC_READY_READY_Busy ) {}
NRF_UICR->APPROTECT = ( ( NRF_UICR->APPROTECT & ~( ( uint32_t )UICR_APPROTECT_PALL_Msk ) ) |
( UICR_APPROTECT_PALL_HwDisabled << UICR_APPROTECT_PALL_Pos ) );
NRF_NVMC->CONFIG = NVMC_CONFIG_WEN_Ren;
while ( NRF_NVMC->READY == NVMC_READY_READY_Busy ) {}
NVIC_SystemReset();
}
NRF_APPROTECT->DISABLE = APPROTECT_DISABLE_DISABLE_SwDisable;
}
However, it only works partially. Before including this code, each time I tried to download & debug with Segger, I would get the usual message "CTRL-AP indicates that the device is secured. For debugger connection the device needs to be unsecured. Note: unsecuring will trigger a mass erase of the internal flash" from the JLink driver. After accepting, the application would download correctly but as soon as the nRF reset itself (part of the application sequence), I lost all trace information, which was extremely inconvenient.
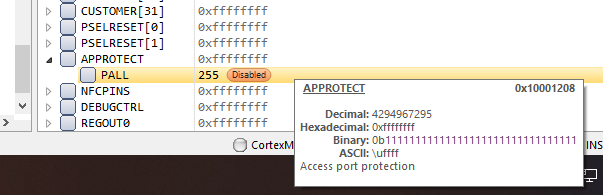
After including this code, I no longer get the message and traces keep working even after a reset. However, if I try to download & debug again, the code doesn't run and the uC seems to be stuck at a random location:
When in this state, I can do an "Erase all" from Segger or --eraseall from nrfjprog, but it doesn't fix the issue. I can only fix it after I send a "nrfjprog --recover" from the command line. After that, the next Segger download & debug works fine.
What could be the issue?
Thank you!