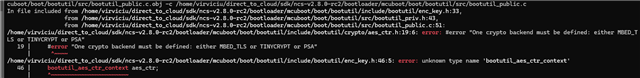
Using v2.8.0-rc2 as v2.7.0 doesn't support the SCRATCH partition.
I am not able to enable BOOT_ECDSA_TINYCRYPT (required for Image Encryption).
I suspect this is because the nRF sysbuild CMake will include external_crypto.conf:
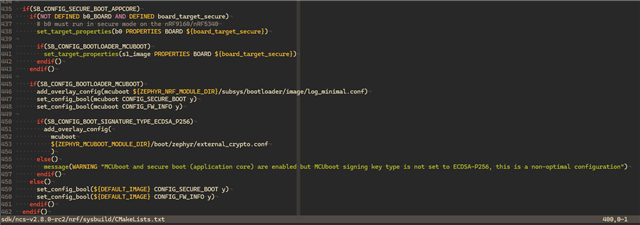
The external_crypto.conf is going to enable BOOT_NRF_EXTERNAL_CRYPTO:
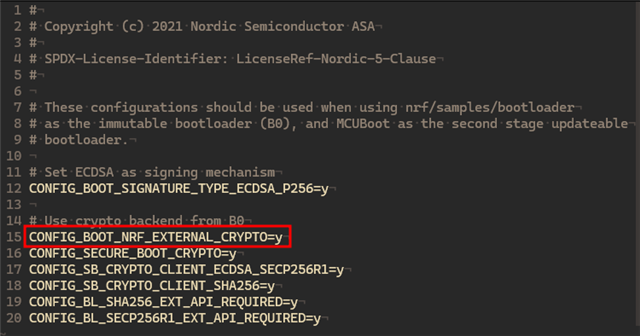
... and this can't be overwritten.
I tried setting the option in <APP_DIR>/sysbuild/mcuboot/prj.conf.
If I comment out CONFIG_BOOT_NRF_EXTERNAL_CRYPTO=y in external_crypto.conf, I am able to modify the value and everything builds successfully. Otherwise, I get spammed with build errors: