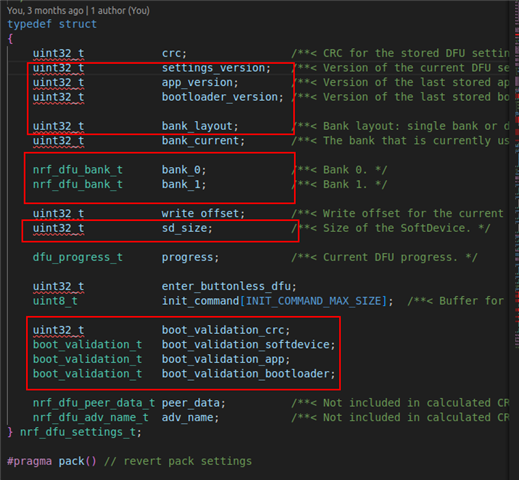
I open up a flash shared space in app and bootloader, write values from app, bootloader read, bootloader read values such as 0xFFFFF, and not ideal values, may I ask why this is.
Based on the background of this problem, I want to customize the protocol OTA without any verification. I have correctly transferred the firmware data to bank1 through flash, and I want to modify s_dfu_setting myself to make the bootloader know that the firmware is valid and can be updated.