Hey,
We have a library (rust) responcible for communicating with the BLE peripheral Using btmgmt dbus messages to bluez.
We have never initiated a dedicated `aagent` in our gateway.
When communicating with BLE device running ncs 270 - we pass pairing phase, and everything works.
But when communicating with device running ncs 280 - the pairing failed, and communication dropped ungracefully.
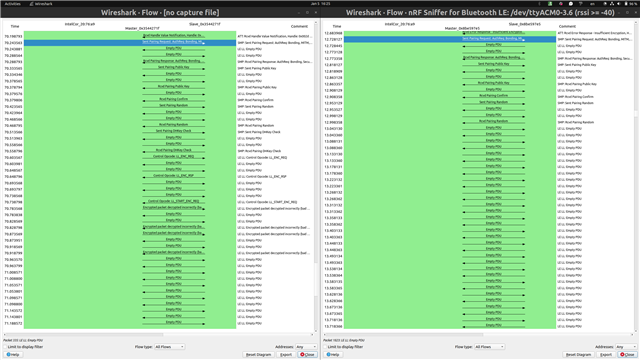
In the picture, we see the SMP pairing phase
Left - client communicating with BLE running ncs270 (we can see DHKey exchange)
right - client communicating with BLE running ncs280 (No DHKey exchange, why?)
To make things work I need to manually select a `agent DisplayYesNo`.
1. What was changed between 280 and 270?
2. Why there's no DHKey exchange with v280 when using default-agent?
3. How can I make it work without triggering dedicated agent?
Thanks
