Hi,
We have a pcap file of a MQTTS connection to AWS, provided by the Soracom SIM console. I will print the first lines of the Wireshark trace so you can see what I am working with.
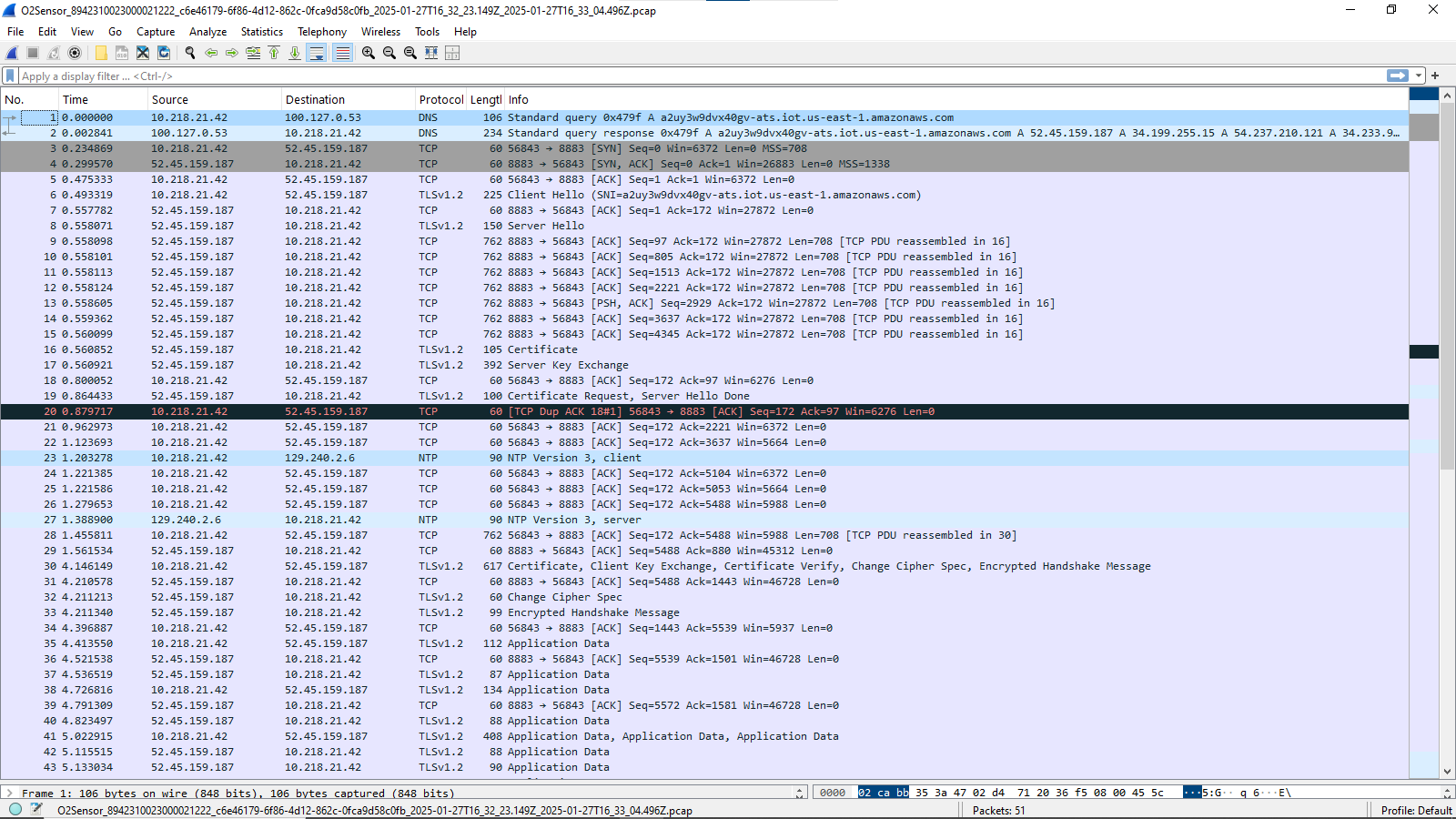
What technique can I use--and it is fine if I have to rebuild my asset_tracker_v2 firmware, and I will be happy to know how to do this with any level of SDK, and it does not have to be asset_tracker_v2, but any application or sample that uses MQTTS would be fine--to allow me to see the unencrypted data rather than the encrypted data for the MQTTS packets. For example, you can see with packet 35 expanded that I am looking at the encrypted data by default:
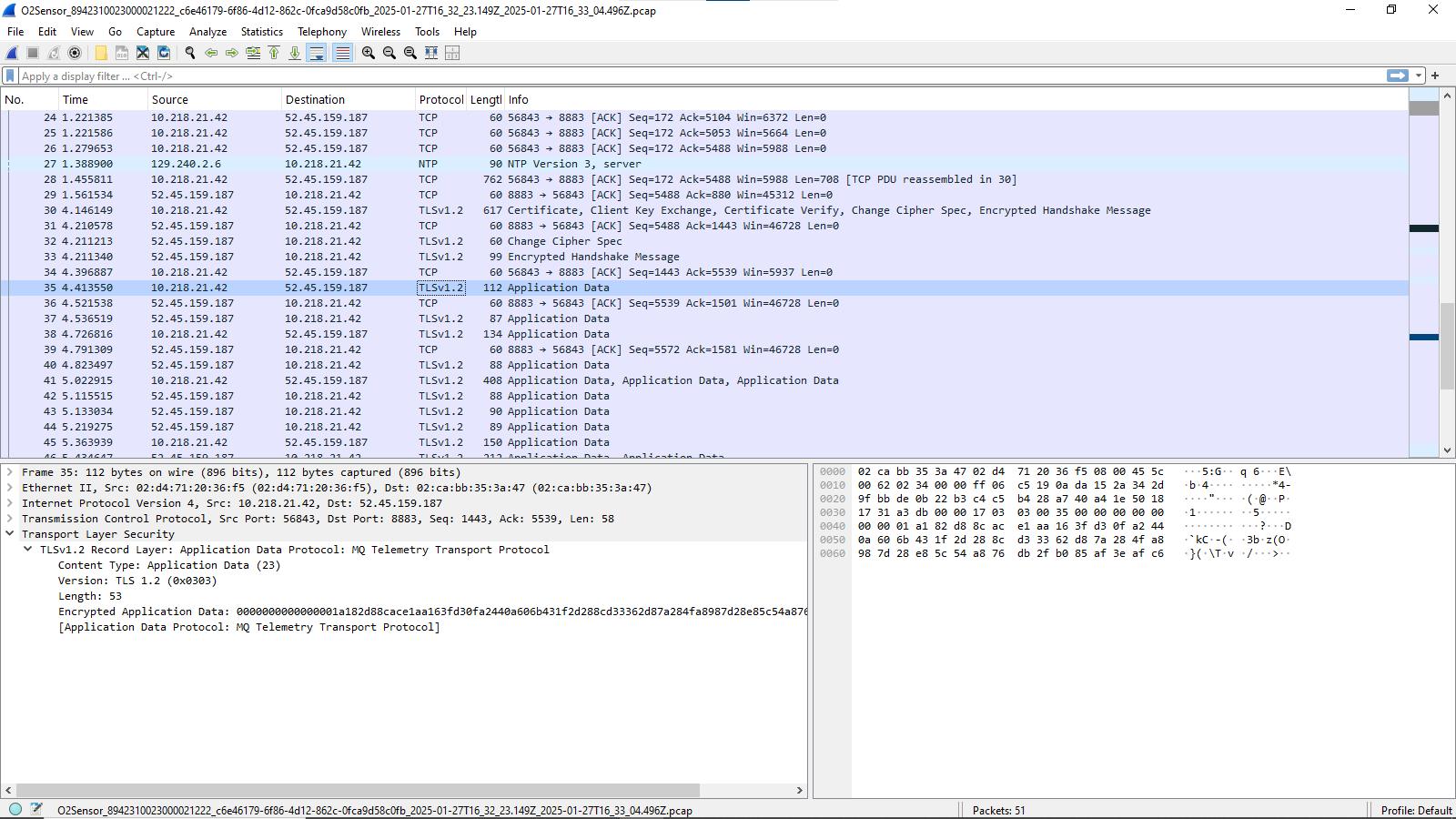
Thank you very much. I know this can be done when the client is a browser on a computer, but I don't know the techniques when TLS is on an embedded device that uses modem firmware, like the nRF9160 we use.
Regards,
Burt Silverman


