Hello,
Platform: nRF54L15, SDK 2.9, VS Code
Our application is Matter + BLE (like NUS) based door lock application. A BLE custom service (adapted from NUS) is used to exchange info in parallel with Matter. We are not encrypting the BLE transmissions and the BLE security level is set to BT_SECURITY_L1. The reason is due to product requirement that our customers do not want to press the "pairing request" notification in the mobile iOS/Android apps. Setting bonding will eliminate this but Matter standard does not allow bonding. Long story to short, we have taken the approach of encrypting the BLE payload.
For encrypting the payload, we are using the standard ECDH + certificate based authentication to derive a key plus authentication:
- After BLE is connected (first time only), the lock and mobile uses ECDH to derive a AES-128 symmetric key, which will be used for encryption and decryption of payload.
- Certificates are exchanged to authenticate further and connection is terminated if certificates are not validated. we plan to use ECDSA which will be next step.
- Key is stored internally and key derivation is not repeated for subsequent connections
- We used PSA CRYPTO libraries.
- Since Matter uses PSA Crypto, we did not include any additional configurations in prj.conf.
Question #1: is there a solution that will allow us to use encryption that comes with BLE stack than we writing the custom encryption (we would prefer BT_SECURITY_L4) but without the iPhone and Android pairing request notifications?I do not believe one exists but we want to ask Nordic to rule this option out.
Q2: When we look look at the ram_report, the SRAM needed for our Crypto application is very small - it is the space needed for variables. It looks like MBEDtls library did not take additional space. Does it look alright? From our reading, the MBEDtls should be a memory hog and should consume large memory while we are not seeing an increase in SRAM usage.. This is the reason for asking this question.
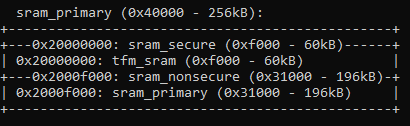
Q3. We tried TF-M (/ns builds), however, we are running out of SRAM. Without TF-M, the SRM usage comes to 220KB. When we try to build with /ns, the build complains that region `RAM' overflowed by 4076 bytes. The TFM configuration is as follows (adapted from DK).
According to the above PM, the tfm takes up only about 8K RAM and we have 30K left. The documentation is sparse so please help to achieve TFM.
Q4. We would like to store the resulting AES-128 bit asymmetric key in the KMU. It is little bit confusing from the readings if it will be possible to store the key in the KMU without TF-M as the documentation is sparse. Assuming that we won't be able to do TF-M, please provide an example, or provide the necessary guidelines for storing the keys and also the certificate in the KMU.
This post says that keys are stored in ITS not in KMU: Using PSA function to persist key in kmu AND later restore it for AES encryption
This post says (1 year old) that KMU has limited functionality: Usage of KMU and CC3XX drivers It is not possible to change the Keys in a slot. Since it is one year old and nRF54L15 is new, is it applicable?
Thanks.
Subu