We use nrf52833 chip but I don't know which SDK and version.
but I used "s113_nrf52_7.2.0_softdevice.hex" in our project having started on 2021.01.27.
So, It's old project starting before.
The problem is as followings:
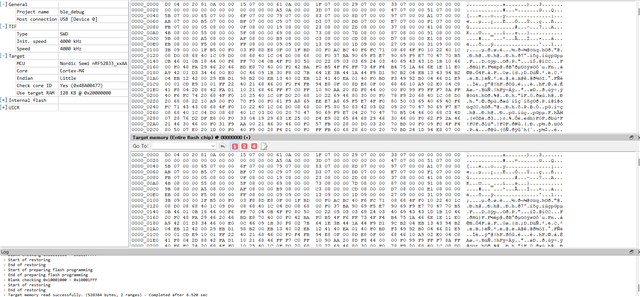
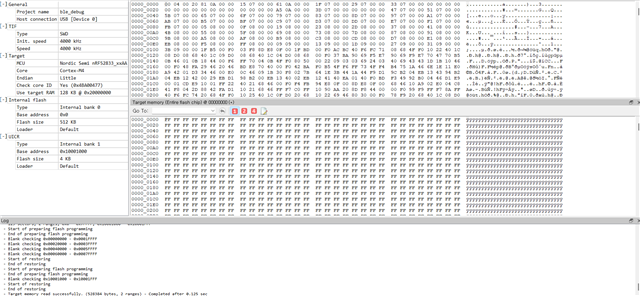
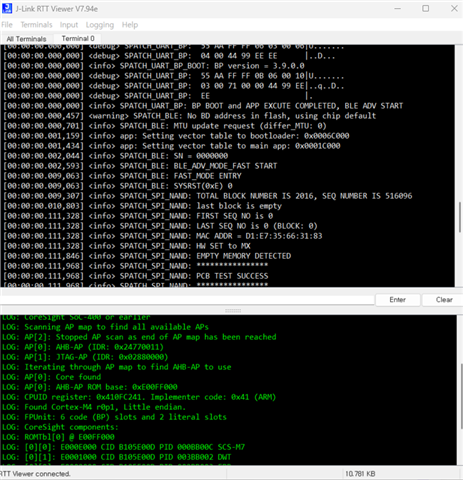
Our target device is connected with RTT Viewer.
However, RTT Viewer dosen't show any log messages from our target device.
Our project's current configuration for RTT logging are as followings on "sdk_config.h" header file.
1. define belows.
2. call on main() function.