Hello Nordic support,
My application is a Zigbee coordinator application on nrf52840 based on nRF5 SDK for Thread and Zigbee v4.2.0. I was able to pair a Zigbee end device to this coordinator without any issues. However, I noticed that after a while, the coordinator sent a Transport Key command to this end device even though the end device did not request for key and after this, the Zigbee end device sent a leave command and left the network.
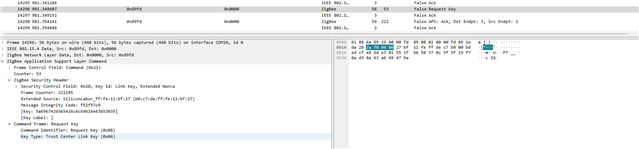
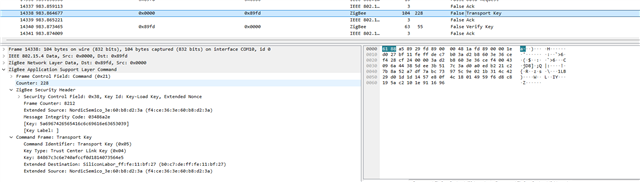
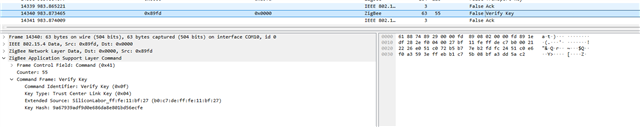
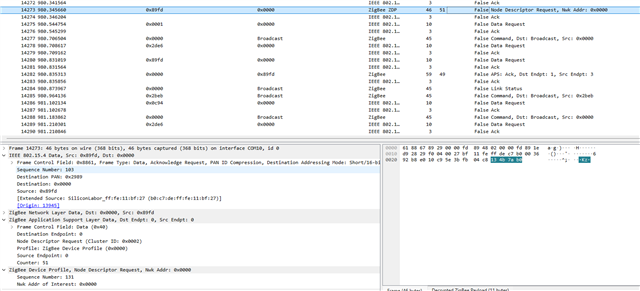
I have attached the Wireshark Zigbee capture where packet number 14456 shows the Transport Key command sent by coordinator and packet number 14463 shows Zigbee end device sending leave command.
Encryption key is 72:C1:C3:89:AD:F4:94:46:94:7F:15:51:07:71:DC:93 (Order Reverse) and Global Zigbee alliance Trust Center Link Key 5A 69 67 42 65 65 41 6C 6C 69 61 6E 63 65 30 39 (Order Normal).
I would like to get information on the following points:
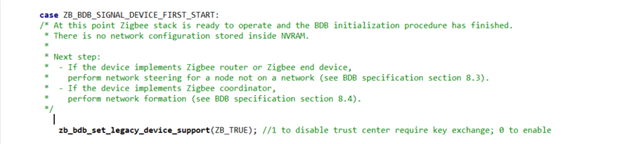
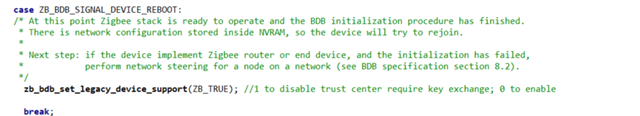
1. On what occasions does the coordinator send Transport Key command without Zigbee end device requesting for Key? Is there a way to simulate this behavior to make the Zigbee coordinator send Transport Key command?
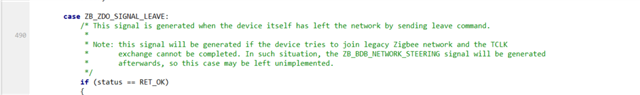
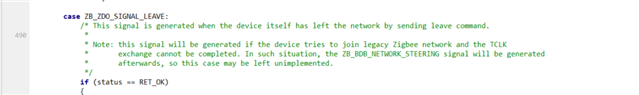
2. Why would Zigbee end device send leave command in response to Transport Key command?
Please let me know if you need more details to help in looking into this issue.
Regards,
Anusha