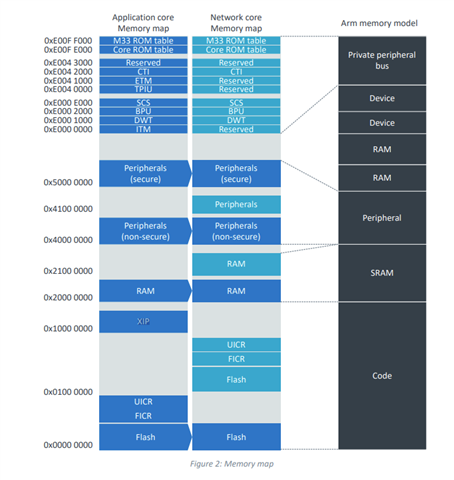
My platform is the NRF5340, coupled with 32MB of external flash, so I have plenty of external storage available.
However, there's a risk that my project may eventually outgrow the internal flash.
Here’s a wild idea—what if both the MCUBoot primary and secondary slots were placed in external flash and executed directly from there?
Would this be feasible, perhaps by leveraging Direct-XIP capability?
I’ve seen some examples where parts of the code (libraries, objects) are executed from an external XIP area, but never the entire codebase.
After some research, it seems that full execution from external flash isn't possible due to certain limitations.
Summing them up (correct me if I’m wrong), functionalities like interrupt handling and Zephyr kernel functions cannot be executed from external flash. Relevant discussions:
However, I’d like to be absolutely sure. Could you provide more details on why this is the case?
Is this fundamentally impossible due to hardware limitations, or is it just challenging to achieve with custom MCUBoot modifications?
Lastly, regarding the security of the external XIP area—how does it compare to an encrypted/signed MCUBoot primary slot in internal flash?
Would it be possible to protect it using TF-M?
Thanks in advance!