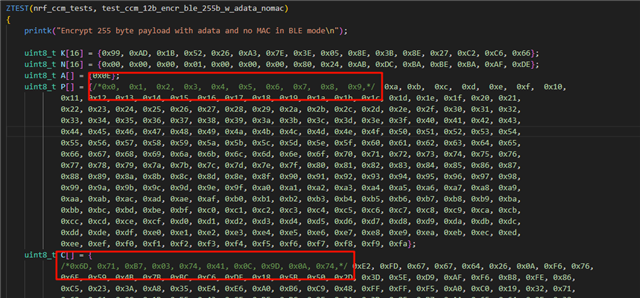
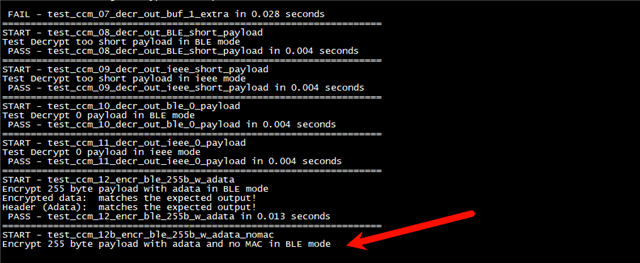
1st problem:
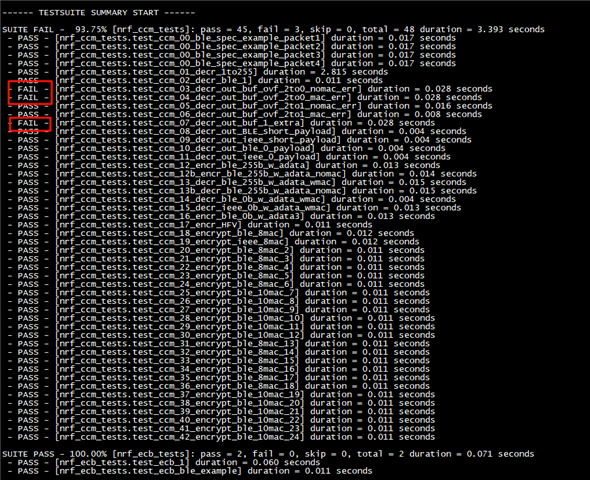
There are some failed case when i run \v2.9.1\modules\bsim_hw_models\nrf_hw_models\tests\zephyr_apps\54_aar_ccm_ecb\src\test_ccm.c
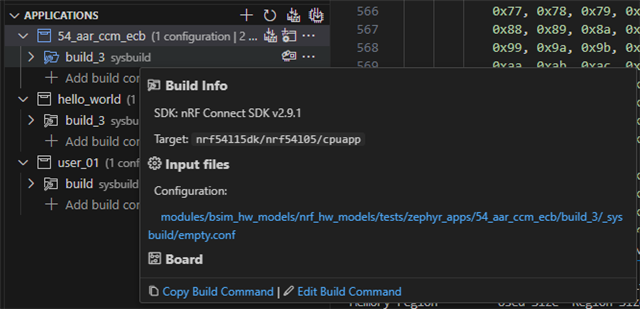
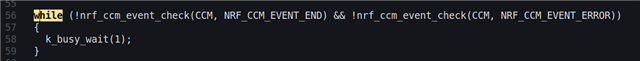
2nd problem:
If I reduce the amount of encrypted data in test_ccm_12b_encr_ble_255b_w_adata_nomac, the encryption process gets stuck.