Hello,
We are working on an NRF5340/NRF7002 based project with NCS 2.7.0 SDK.
We have been able to get Amazon Root CA 1 and 3 working with the following .conf:
# Wifi is nrf7002 based CONFIG_WIFI=y CONFIG_WIFI_NRF700X=y CONFIG_NRF700X_P2P_MODE=n CONFIG_NRF700X_MAX_TX_PENDING_QLEN=12 CONFIG_NRF_WIFI_IF_AUTO_START=n CONFIG_NRF_WIFI_LOW_POWER=y CONFIG_NRF_WIFI_RPU_RECOVERY=y # WPA supplicant CONFIG_WPA_SUPP=y CONFIG_WPA_SUPP_CRYPTO_WEP=n CONFIG_WPA_SUPP_NO_DEBUG=y # Networking CONFIG_NETWORKING=y CONFIG_NET_SOCKETS=y CONFIG_NET_SOCKETS_POSIX_NAMES=y CONFIG_NET_IPV4=y CONFIG_NET_IPV6=y CONFIG_NET_UDP=y CONFIG_NET_TCP=y CONFIG_NET_DHCPV4=y CONFIG_NET_CONFIG_SETTINGS=n # CONFIG_NET_CONFIG_INIT_TIMEOUT=0 # CONFIG_NET_CONFIG_AUTO_INIT=n CONFIG_NET_NATIVE=y CONFIG_DNS_RESOLVER=y # Need 16 FDs for WiFi CONFIG_POSIX_MAX_FDS=16 # Net Management CONFIG_NET_L2_ETHERNET=y # This is mandatory even for WIFI CONFIG_NET_L2_WIFI_MGMT=y CONFIG_NET_MAX_CONTEXTS=4 CONFIG_NET_SOCKETS_OFFLOAD=n // HTTP CONFIG_HTTP_CLIENT=y CONFIG_NET_TCP_KEEPALIVE=y CONFIG_JSON_LIBRARY=y CONFIG_BASE64=y CONFIG_OHTTP_SIGNATURE=y CONFIG_TINYCRYPT_SHA256_HMAC=y #TLS CONFIG_NET_SOCKETS_SOCKOPT_TLS=y CONFIG_TLS_CREDENTIALS=y CONFIG_MBEDTLS=y CONFIG_MBEDTLS_RSA_C=y CONFIG_MBEDTLS_SSL_SERVER_NAME_INDICATION=y CONFIG_PSA_WANT_KEY_TYPE_RSA_PUBLIC_KEY=y CONFIG_PSA_WANT_RSA_KEY_SIZE_2048=y CONFIG_MBEDTLS_ENABLE_HEAP=y CONFIG_MBEDTLS_HEAP_SIZE=61440 CONFIG_MBEDTLS_DEBUG=n CONFIG_MBEDTLS_DEBUG_C=n
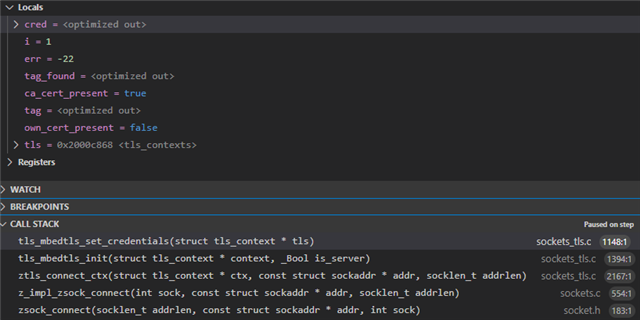
Now with this config when I replace Amazon Root CA 1 and 3 by the 2 and 4, I always get a -22 error on the socket opening.
The examples I found in the DevAcademy uses Amazon Root CA 1 and I did not found any document explaining how to make it work with certificate using "sha384WithRSAEncryption" like amazon root CA 2 and "ecdsa-with-SHA384" like Amazon root CA 4.
I have tried playing with different setting in the .conf with no success...
Is there any kConfig combination that is recommended, an example or a documentation that could help us with this issue ?
For information, credentials are added using "tls_credential_add", certificate are converted from .pem to const uint8_t * see attached files