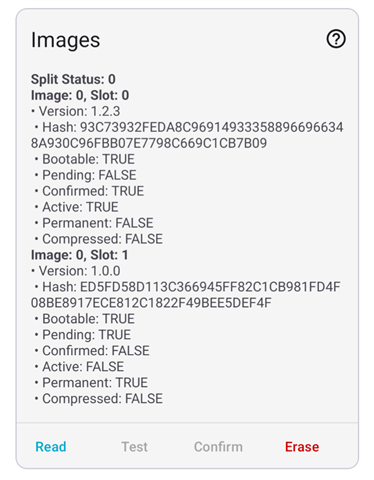
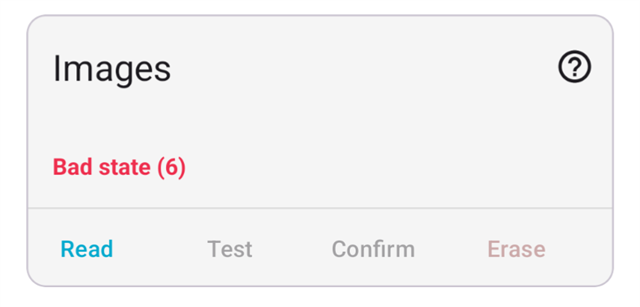
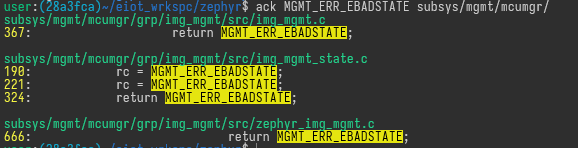
Hi, I have issue where the slot 1 image seems stuck. It can not be erased, confirmed, or swapped in the state that it is currently on. When I click erase, the error bad state 6 will show. As per the error code, the source has this definition "The device is not currently in a state to handle the request.
This firmware image is thoroughly tested in production and has been working for 2 years. The version is stable and supports the SMP server version and implementation same as in the other version on slot 1 and slot 0.
Can the slot 1 still be recovered in some way?
nrf sdk v2.4.2
nrf device manager