Hi
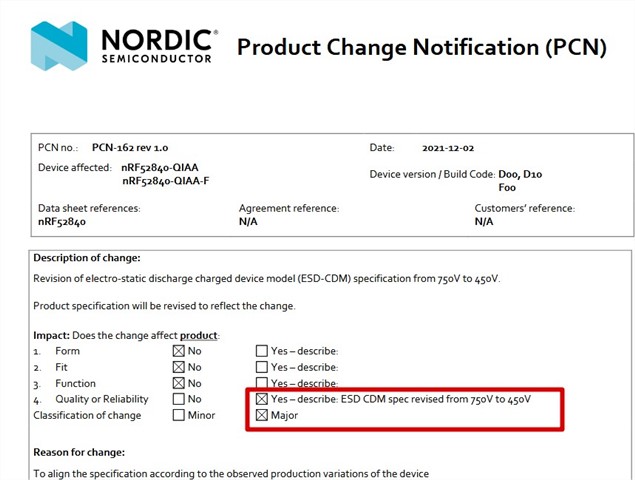
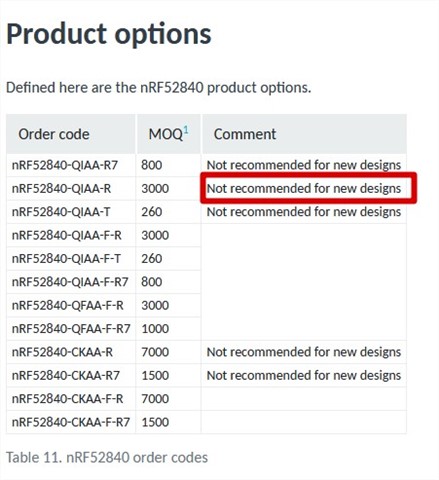
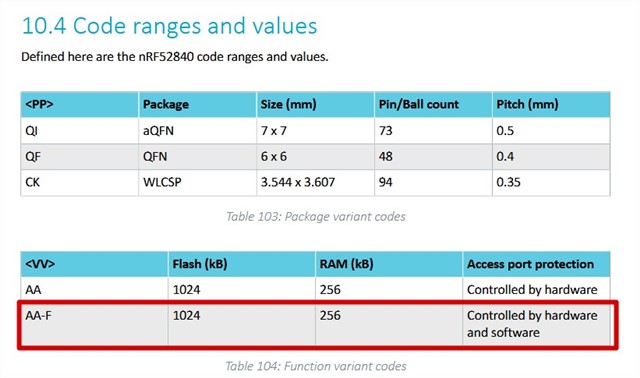
We are using the nRF52840-QIAA-R in a lot of PCBA, now I see there is a new revision nRF52840-QIAA-F-R and the old type is not recommended for new design.
What is the difference between the 2 types and are they 100% compatible? Where can I see the difference between the old and the new type?
Thank you