Hi, I mostly use the SDK 7.2 or SDK 10 and S110 7.1 or 8.0
since I have multiple custom boards that uses revision 2 and 3 chips.
My custom board I'm about to use has no displays or buttons so I use this settings.
sd_ble_gap_sec_params_t sec_params;
sec_params.io_caps = BLE_GAP_IO_CAPS_DISPLAY_ONLY;
My custom board uses nRF51822-QFAA and it is connected to Texas Instrument's MCU (TM4C123GH6PM) to commuciate via UART.
I have questions about passkey example from github.
1) Does passkey always require bonding?
Although I saw the Passkey Entry Diagram, I'm thinking of a scenario that
each side (central like iPhone and the peripheral) don't leave each IRK and address.
So I'm wondering it is okay to use pairing with passkey.
Also, when using passkey, does this always require MITM protection?
sd_ble_gap_sec_params_t sec_params;
memset(&sec_params, 0, sizeof(sec_params));
sec_params.timeout = 30;
sec_params.bond = 1;
sec_params.mitm = 1;
sec_params.io_caps = BLE_GAP_IO_CAPS_DISPLAY_ONLY;
-
About this part,
uint8_t passkey[] = "123456"; // The question is about this value ble_opt_t ble_opt; ble_opt.gap.passkey.p_passkey = &passkey[0]; uint32_t err_code = sd_ble_opt_set(BLE_GAP_OPT_PASSKEY, &ble_opt);
does the passkey has to be numbers (ASCII 0, 0x30 ~ 9, 0x39)?
I tried to use uint8_t passkey[] = "ABCDEF"; instead but sd_ble_opt_set returned an error.
- I'm about to change the
uint8_t passkey[] = "123456";using a timer that timeouts every 30 minutes like the following picture peridocially.
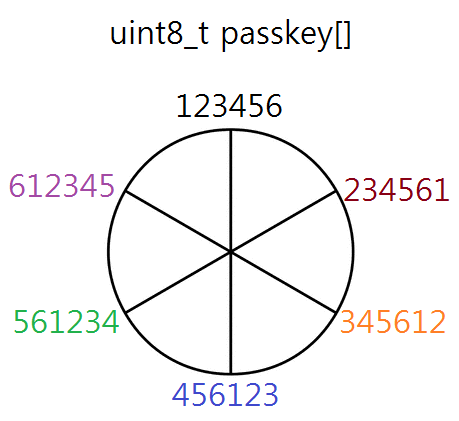
Suppose I connected this peripheral with my iPhone when the passkey value was 345612.
After resetting the peripheral, the passkey will be 123456.
In this state (passkey equal to 123456), when my phone requests connection,
(since my phone used passkey 345612 in the past) will it connect? I hope I can get the reason too.
- If pairing + passkey is not possible, then I'm thinking of "phase shifting".
In detail, I'm thinking something like this since BLE blacklisting is impossible.
I want specific phones (let's say this is group A) to bond (with passkey) to my peripheral by triggering GPIO pins using the TM4C MCU.
When the TM4C is not triggering, then the nRF chip uses pairing with NUS, knowing that group A will not request connections and other phones will request connection.
Then do I need to call sd_softdevice_disable for "changing the phase" (passkey bonding - NUS pairing).
-Best Regards, Mango
