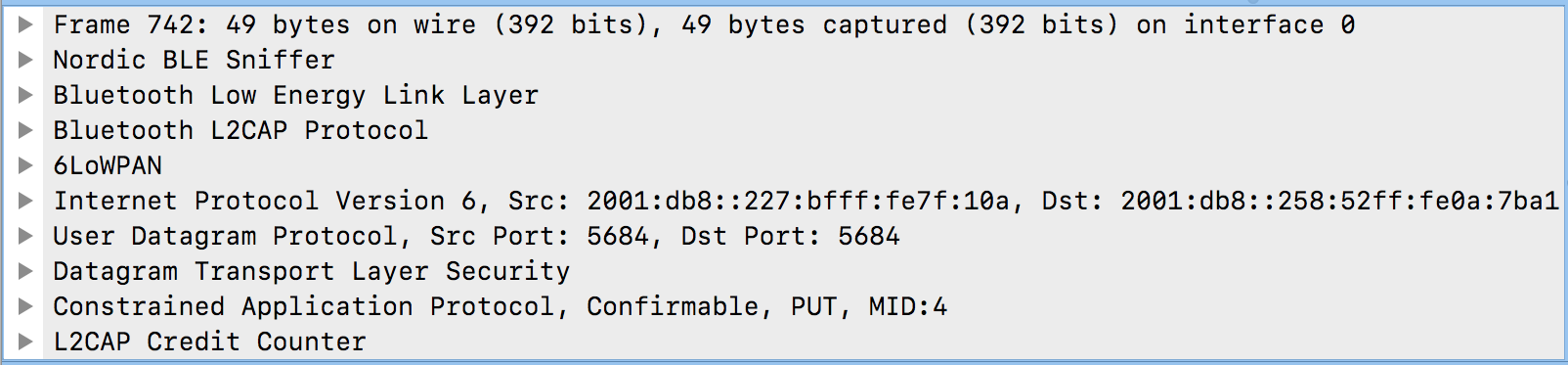
I'm using the latest SDK (14.1) and have got a working COAP server running over BLE on a nRF52DK, and can exercise the service from my Ubuntu desktop without any problem.
I have a separate windows machine running the Nordic sniffer which I've been using successfully to sniff GATT data.
Is is possible to configure Wireshark to decode the 6lowpan traffic over BLE, if so how.
At the moment I can see the connect request, but no more. I'm not sure if I'm just missing a configuration step, or if there's some fundamental piece not missing. I can't believe I'm the first person to try this, but I don't see anyone else asking the same question.
Any suggestions?
Thanks.